AWS - a Cloud Computing Solution for Startups
Watch the Configuration Video
Project Requirements
Company Background: A Medical Company
- A Medical Company is a startup software as a service (SaaS) company.
- It has built an online medical social networking and diagnosis assistance application for users in APAC, the US, and Europe.
- HA Zones: APAC (Asia-Pacific), the US, and Europe
- Redundant Gateway
- The application connects patients and doctors to:
- Allow online appointments, remote consultation, remote diagnosis, electronic prescription transfer, and payment services.
- Allow customers to upload documents and images. Text is extracted from documents, and images are converted into multiple formats.
- The application has not yet been launched publicly.
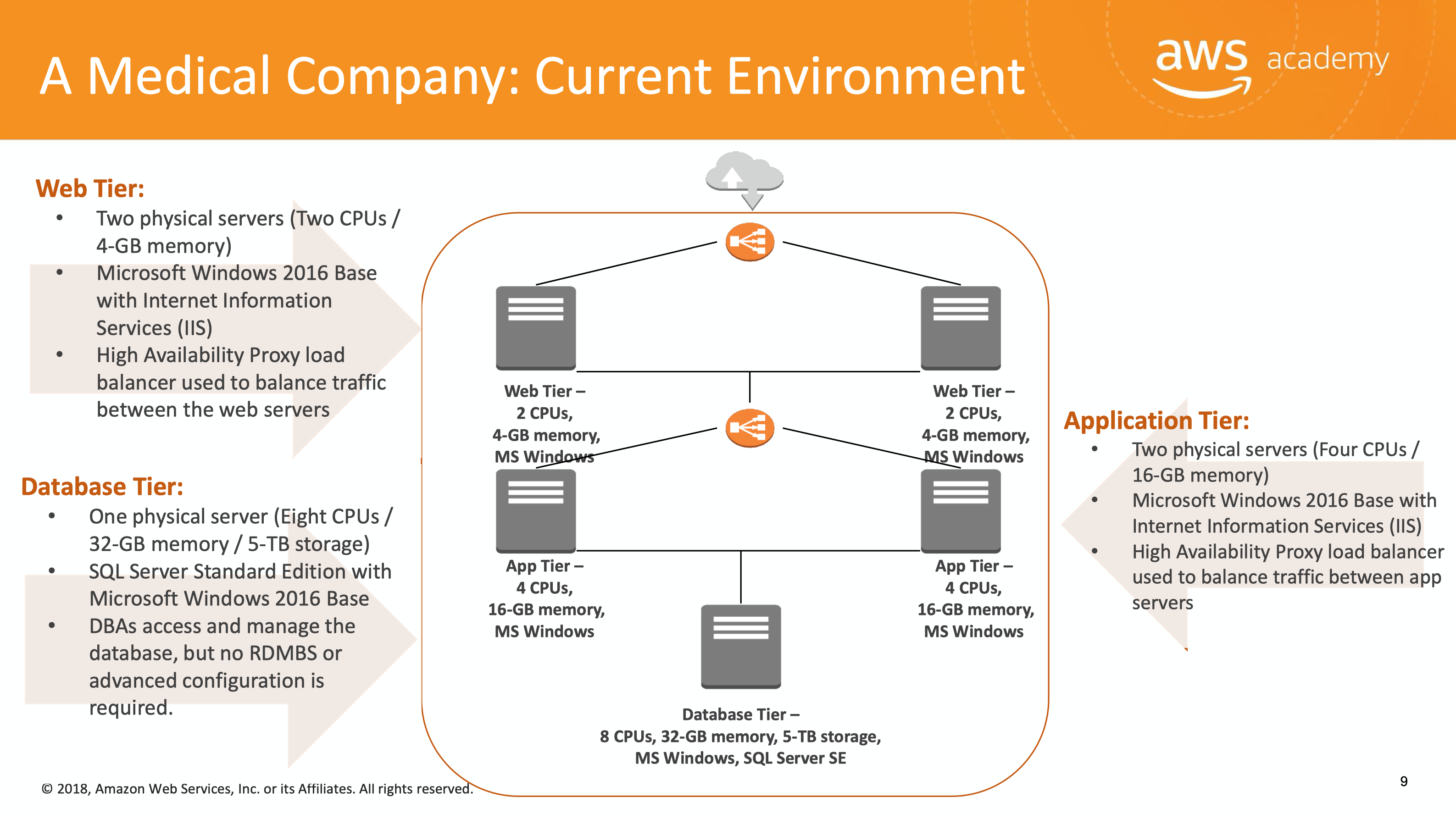
Current Environment
For your preparations, the customer provided this information on their current environment. A Medical Company:
- Deployed it’s current development and test infrastructure with a server hosting company.
- Uses Microsoft Windows servers to host their web and application tiers with Microsoft SQL Server Standard Edition backend databases.
- The application launch date is coming soon and they expect many users to start using the application.
- Believes it would be best to use cloud technologies to support its rapid growth.
- Thinks the new cloud platform could host the development, test, and production environments.
The requirements include:
- Configuring access permissions to conform with AWS best practices.
- Building networks that conform to AWS best practices while providing all the necessary network services to the application in their different environments.
- Building an architecture that matches the current architecture at the server hosting company and that can handle doubling the number of servers.
- Securing all medical information, as medical information usually contains highly sensitive personally identifiable information (PII).
- Utilizing load balancers for web tier and application tier that must support HTTP, HTTPS, TCP protocols plans to move their application into AWS.
- Architecture should be resilient (built for business continuity).
- Configuring auditing to track all user actions.
Additionial Requirements:
- High Availability: Overall, your architecture should design for High Availability (make sure you understand the definition). I would suggest using a goal of 99.9% for the HA objective, Use that criteria to influence your decisions.
- Availability Zone(s): In the context of #1 above, how do the AZs and regions factor in to the HA design that will allow you to achieve the desired goal. Make sure to factor that into your design and if there are any limitations, point them out as potential risks.
- Load Balancing vs Elasticity: In your architectural design make sure to indicate where you are using Load Balancing techniques versus Elasticity AND for what purpose you are using those techniques (whether they are used together or not).
- Sensitive Information: Here we will NOT use specific regulations, but we will more generally treat the information we are collecting as sensitive (protected). That said, your architecture needs to support the protection of sensitive information throughout its entire lifecycle (information capture, information processing, information sharing, information destruction)
- Monitoring and Analysis: Your design needs to account for the monitoring of your application/infrastructure components. You do not have to identify the specific metrics captured, however, you should identify the categories of metrics collected by the services that you plan on using. Finally, indicate how you will ANALYZE the data collected during monitoring to help to achieve “Operational Excellence”.
Services & Configuration Summary
Topology
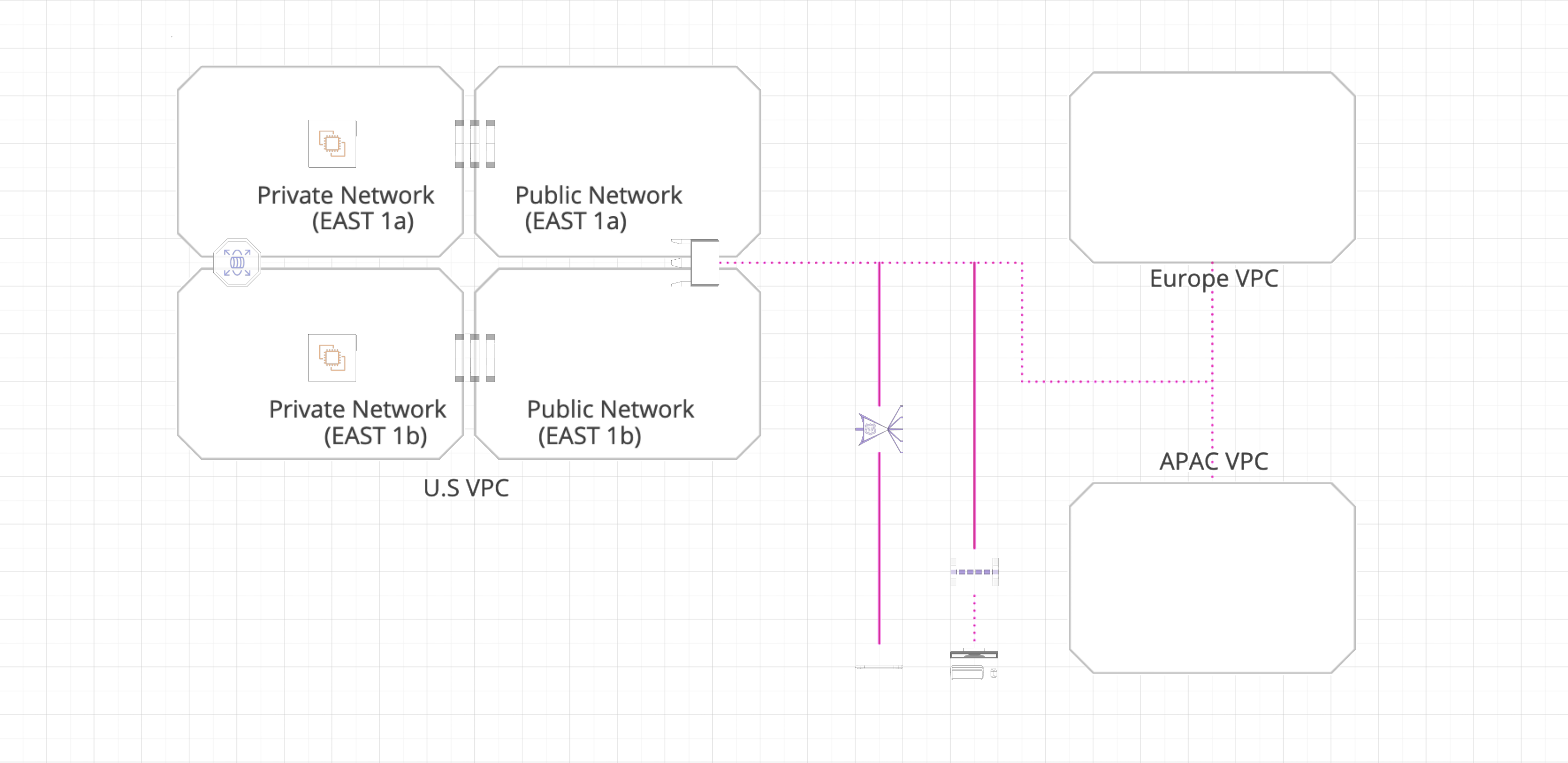
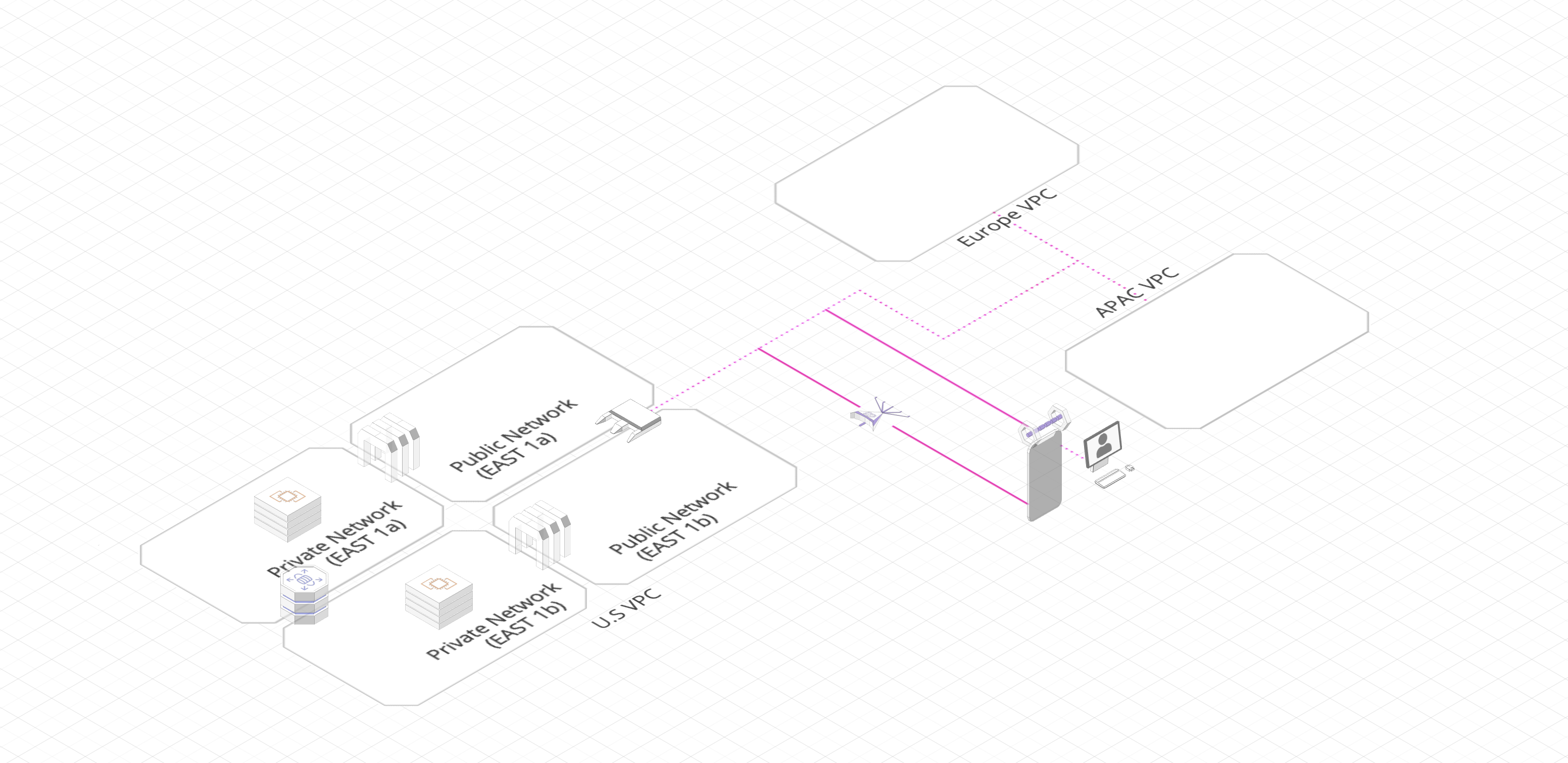
the U.S VPC
VPC, Isolated cloud resources, simulate a complete local network environment, which is the foundation and prerequisite of running most of the Amazon Web Services.
the MC - VPC - US - EAST - 1: 10.0.0.0/16
- Subnets:
US - EAST - 1a(Public Subnet):10.0.0.0/24US - EAST - Web - 1a(Private Subnet for WEB):10.0.2.0/24US - EAST - App - 1a(Private Subnet for Application, currently unused):10.0.3.0/24US - EAST - 1b(Public Subnet):10.0.128.0/24US - EAST - Web - 1b(Private Subnet for WEB):10.0.130.0/24US - EAST - App - 1b(Private Subnet for Application, currently unused):10.0.131.0/24- Route Tables
Public Route TableWeb Route Table - 1aWeb Route Table - 1b
- Internet Gateways
US - EAST - IGW
- NAT Gateways
NGW - 1a: inUS - EAST - 1aNGW - 1b: inUS - EAST - 1b
- Peering Connections
US - EAST - 1 to EU - WEST - 2: connect two VPCs
- Security Groups
Connect: forConfiguration Severthat locates inUS - EAST - 1aDB: for RDSIntranet: forWEB ServerWEB: forWEB Server
Europe VPC
VPC, Isolated cloud resources, simulate a complete local network environment, which is the foundation and prerequisite of running most of the Amazon Web Services.
the MC - VPC - EU - WEST - 2: 20.0.0.0/16
- Subnets:
EU - WEST - 2a(Public Subnet):20.0.0.0/24EU - WEST - Web - 2a(Private Subnet for WEB):20.0.2.0/24EU - WEST - App - 2a(Private Subnet for Application, currently unused):20.0.3.0/24EU - WEST - 2b(Public Subnet):20.0.128.0/24EU - WEST - Web - 2b(Private Subnet for WEB):20.0.130.0/24EU - WEST - App - 2b(Private Subnet for Application, currently unused):20.0.131.0/24
- Route Tables
Public Route TableWeb Route Table - 2aWeb Route Table - 2b
- Internet Gateways
EU - WEST - IGW
- NAT Gateways
NGW - 2a: inEU - WEST - 1aNGW - 2b: inEU - WEST - 1b
- Peering Connections
EU - WEST - 2 to US - EAST - 1: AUTOMATICALLY generate if you set up it in the U.S VPC.
- Security Groups
Connect: forConfiguration Severthat locates inEU - WEST - 2aDB: for RDSIntranet: forWEB ServerWEB: forWEB Server
the U.S EC2
EC2, Virtual servers in the cloud, is a server running your OS and application.
- Instances:
Web Configuration: 1, in public subnet for SSH login.web-tier: 2, in private subnets providing web service.
- AMIs
Web Template.ver2: created from EC2 instanceWeb Configuration, for new instances that will be launched in the future.
- Load Balancing (AWS Elastic Load Balancing)
- Load Balancers
US-EAST-ELB: the ELB configuration template.
- Target Groups
US-EAST: define the groups that will apply the ELB configuration template.
- Load Balancers
- Auto Scaling:
- Launch Configurations
Web Configuration: the HA configuration template.
- Auto Scaling Groups:
Web Application: define the groups that will apply the HA configuration template.
- Launch Configurations
Europe EC2
EC2, Virtual servers in the cloud, is a server running your OS and application.
- Instances:
Web Configuration: 1, in public subnet for SSH login.web-tier: 2, in private subnets providing web service.
- AMIs
Web Template.ver2: created from EC2 instanceWeb Configuration, for new instances that will be launched in the future.
- Load Balancing (AWS Elastic Load Balancing)
- Load Balancers
EU-WEST-ELB: the ELB configuration template.
- Target Groups
EU-WEST: define the groups that will apply the ELB configuration template.
- Load Balancers
- Auto Scaling:
- Launch Configurations
Web Configuration: the HA configuration template.
- Auto Scaling Groups:
Web Application: define the groups that will apply the HA configuration template.
- Launch Configurations
the U.S RDS
RDS, Managed relational database service for MySQL, PostgreSQL, Oracle, SQL Server, and MariaDB, is a server running your database. You do not need create a server and install database again.
- Databases
mcmysql: inMC - VPC - US - EAST - 1
Europe RDS
RDS, Managed relational database service for MySQL, PostgreSQL, Oracle, SQL Server, and MariaDB, is a server running your database. You do not need create a server and install database again.
The RDS located in the U.S VPC could be visited from Europe VPC because of Peering Connections. So there is no RDS in Europe VPC. But it could be.
Global Route 53
Route 53, Scalable domain name system (DNS), is a DNS service of AMS. You can purchase, update, and maintain your domain name in AWS.
- Hosted zones
- zacks.cloud
- http://us.zacks.cloud:
US-EAST-ELB - http://eu.zacks.cloud: eu-west-alb-100765890.eu-west-2.elb.amazonaws.com
- http://us.zacks.cloud:
- zacks.cloud
Direct Connect (Not available now)
Direct Connect, Dedicated network connection to AWS, is a VPN-liked service providing a secure connection between the endpoint and each VPCs. The staff of the company could use it to log in to their intranet.
S3 (Not available now)
S3, a Scalable storage in the cloud, is for storing files not table.
CloudFront (Not available now)
CloudFront, Global content delivery network, is a CDN service for improving the quality of connection between your data center and your users.
CloudWatch (Not available now)
CloudWatch, Monitor resources and applications, provides a friendly UI showing your AWS resource.
An AWS Cloud Computing Solution for Startups
VPC Settings:
Introduction
VPC Settings are one of the most important parts of a cloud computing environment. I distribute 10.0.0.0/16 to US - EAST - 1 and 20.0.0.0/16 to EU - WEST - 2. Basically, other features are same except one thing: our database in US - EAST - 1 for safety. But EU - WEST - 2 could access it. And I will not show the similar settings.
Subnets
US - EAST - 1a: the first subnet (public subnet: 10.0.0.0/24)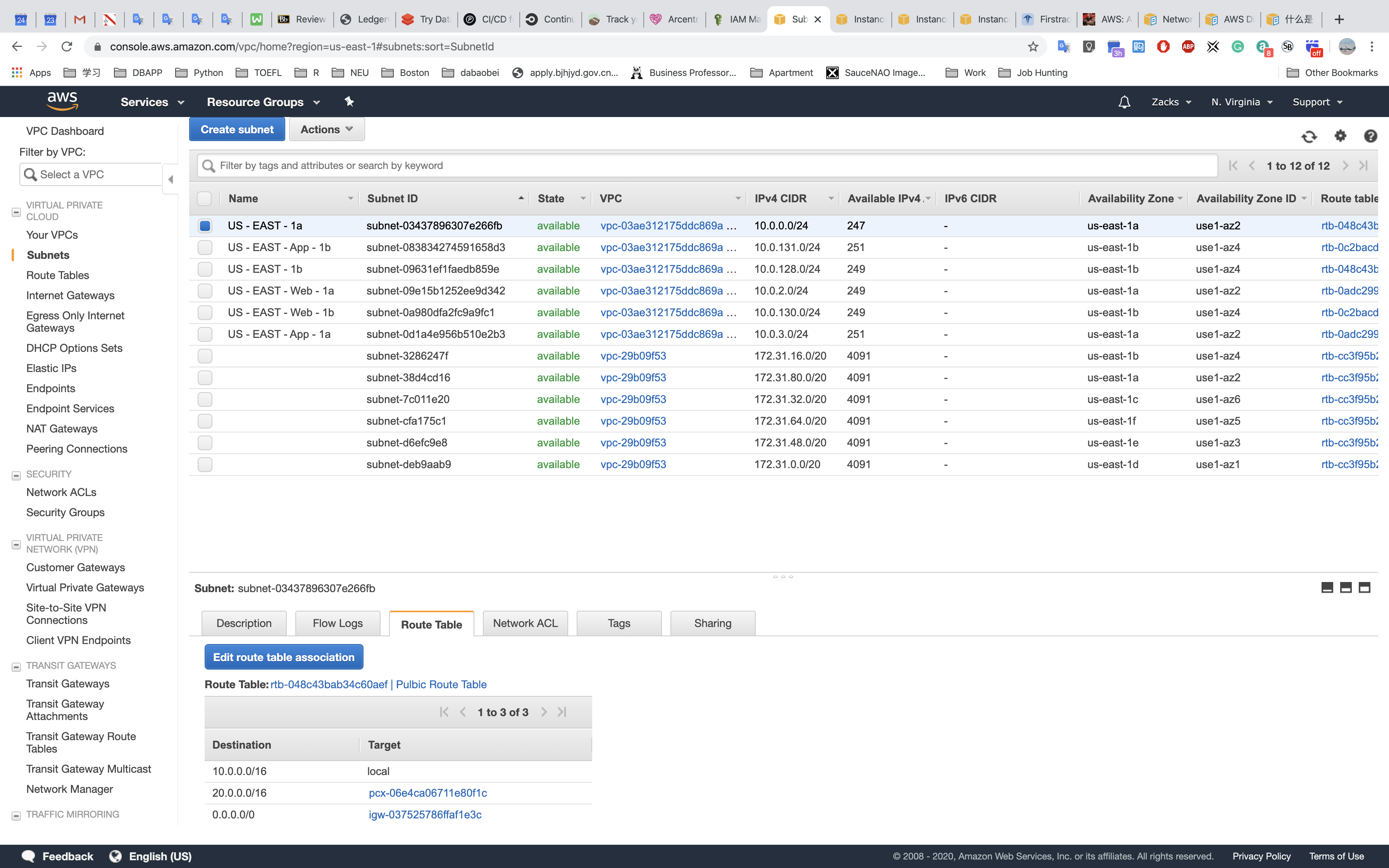
US - EAST - Web - 1a: Web tier (private subnet: 10.0.2.0/24)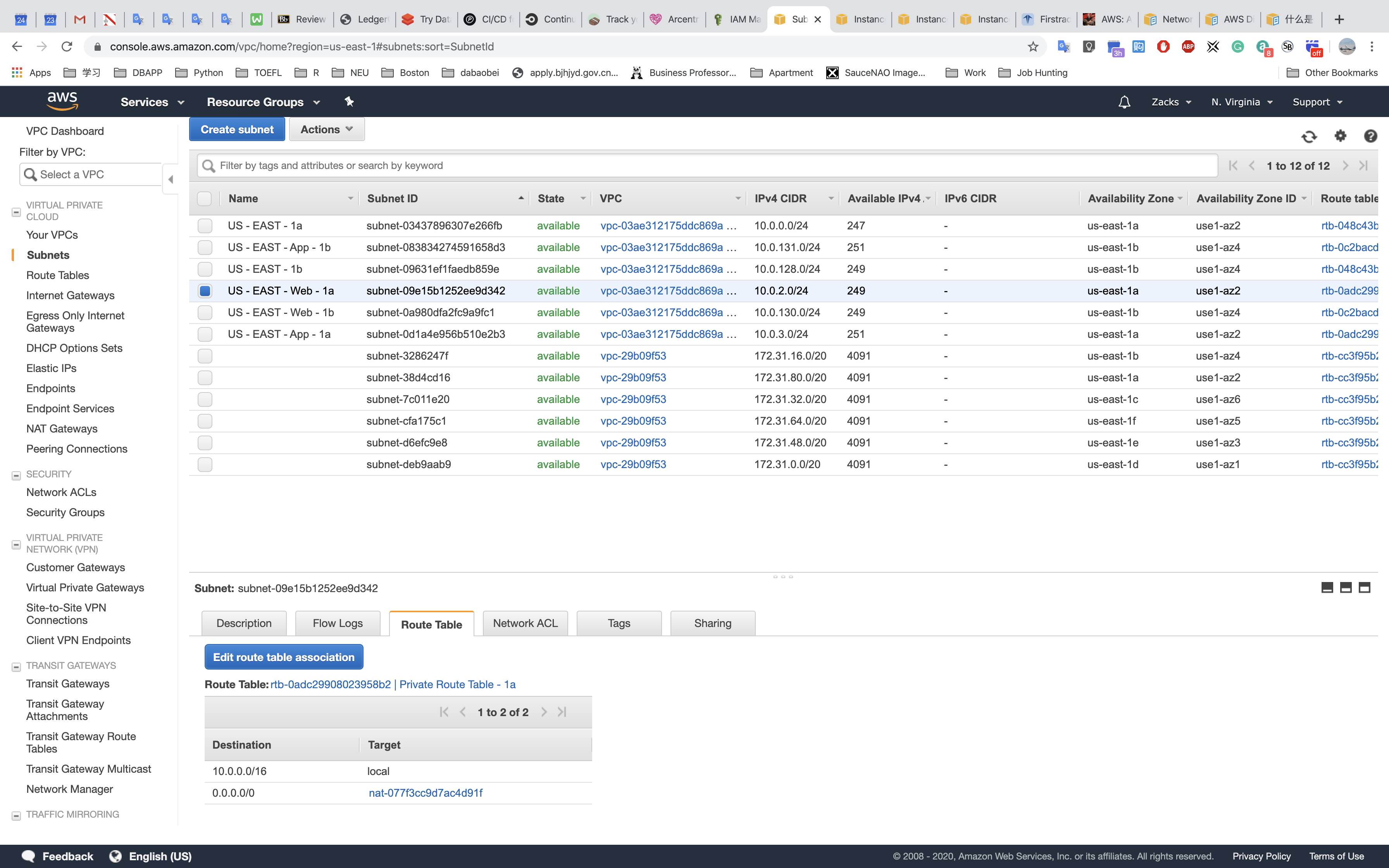
US - EAST - App - 1a: Web tier (private subnet: 10.0.3.0/24)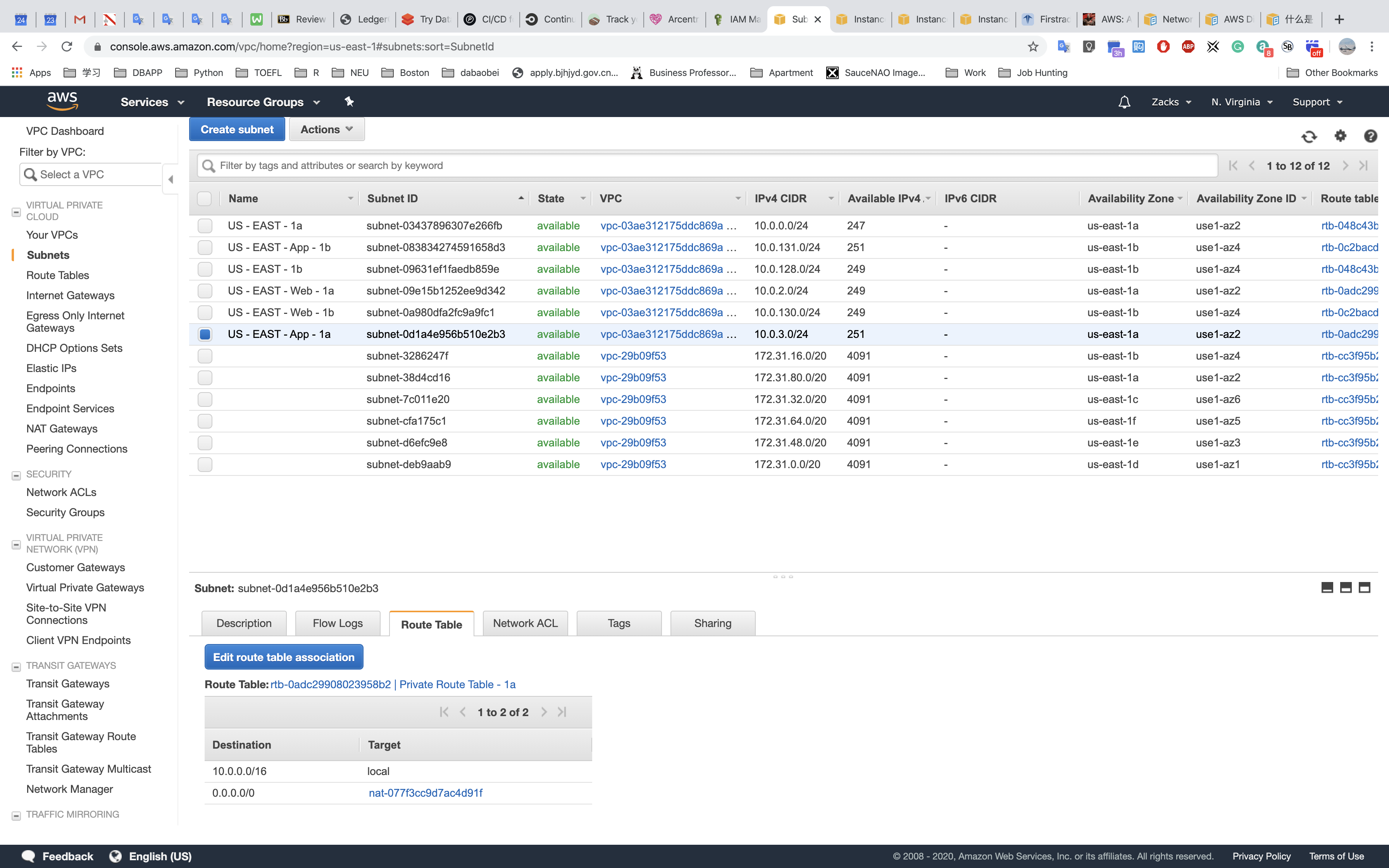
US - EAST - 1b: the second subnet for load balancer (public subnet: 10.0.128.0/24)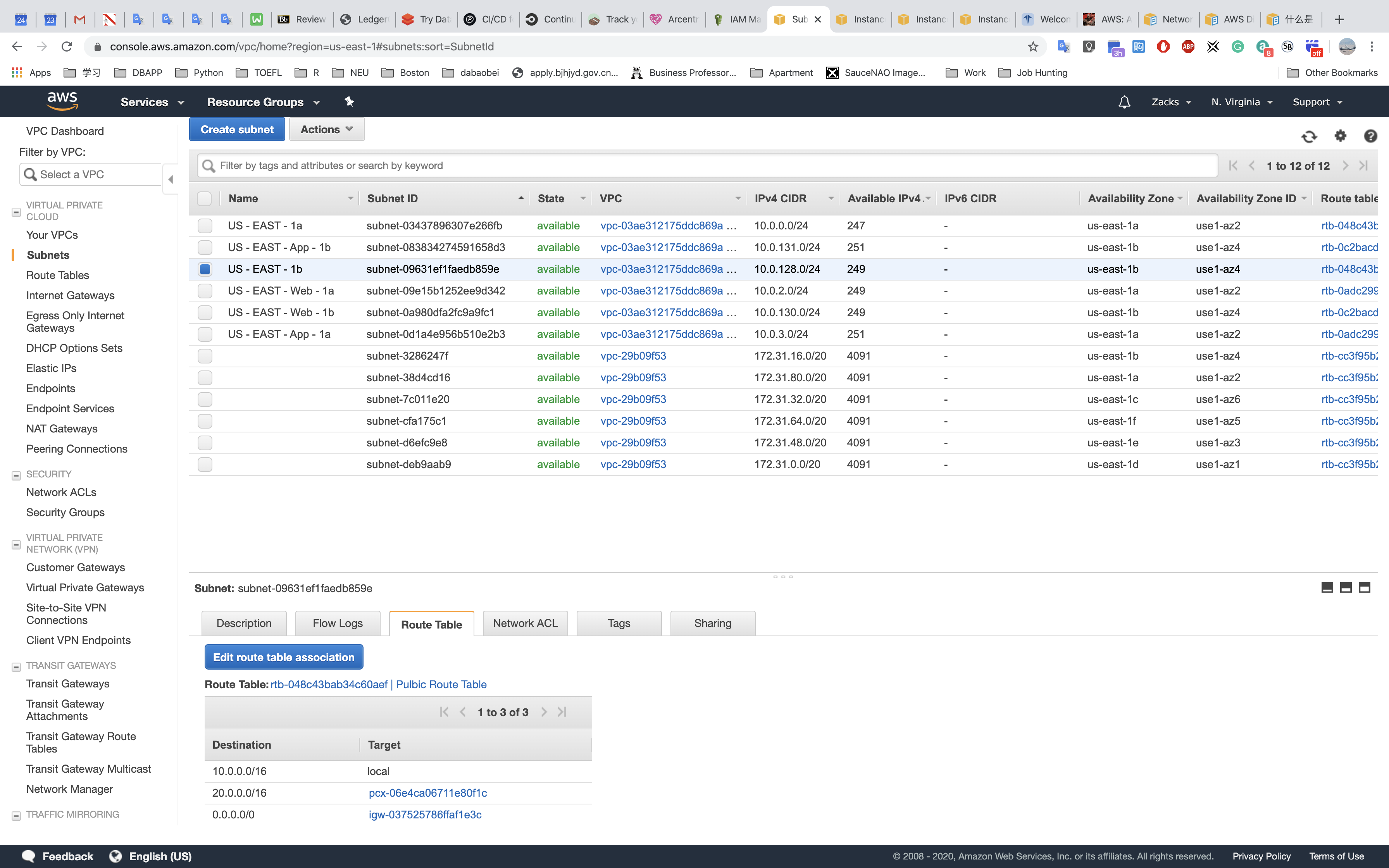
Auto-assign IP address for each EC2 instance in the private subnet that connected to NAT gateway and for EC2 instances that locate in the public subnet.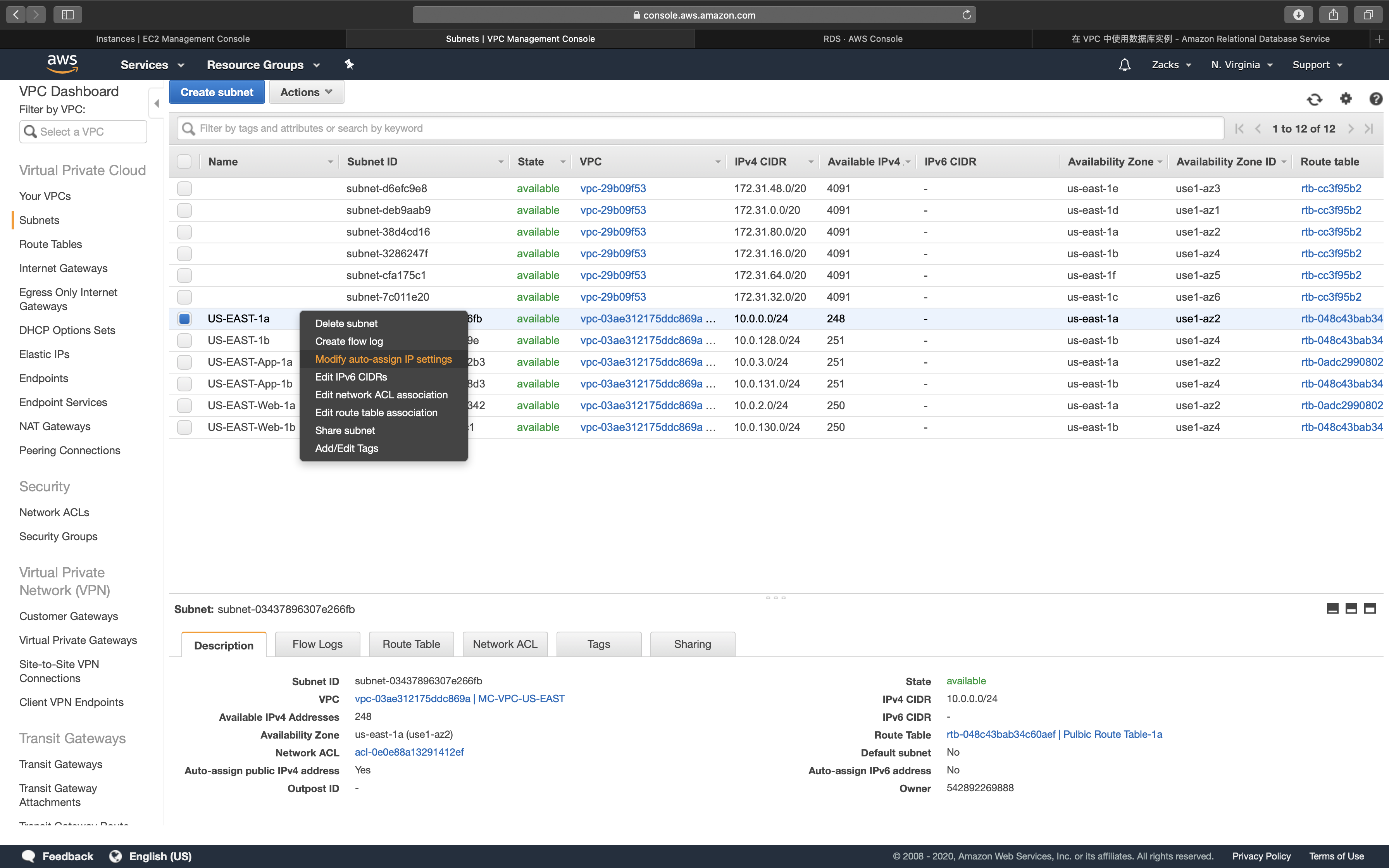
Gateways
Internet Gateway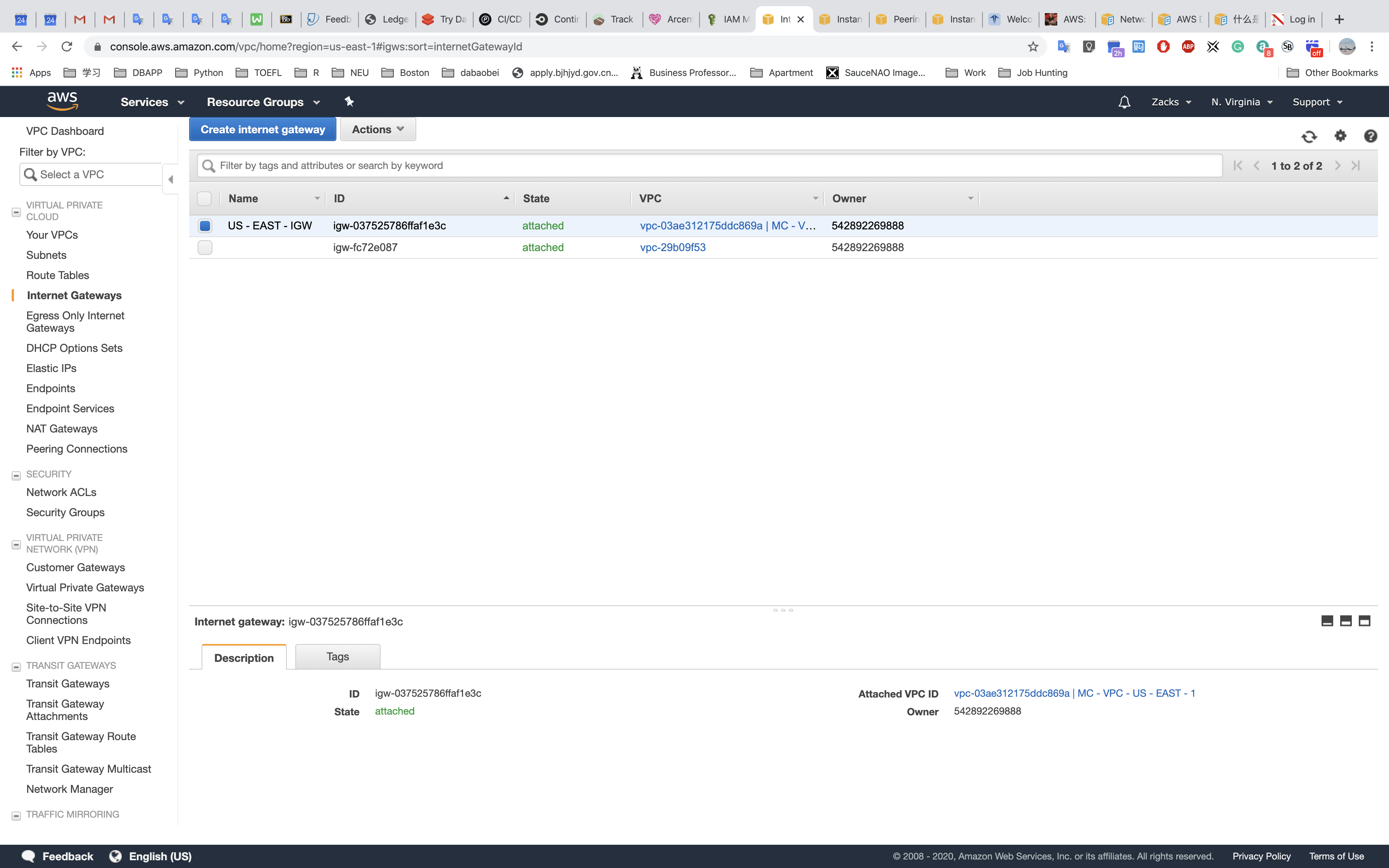
NAT Gateway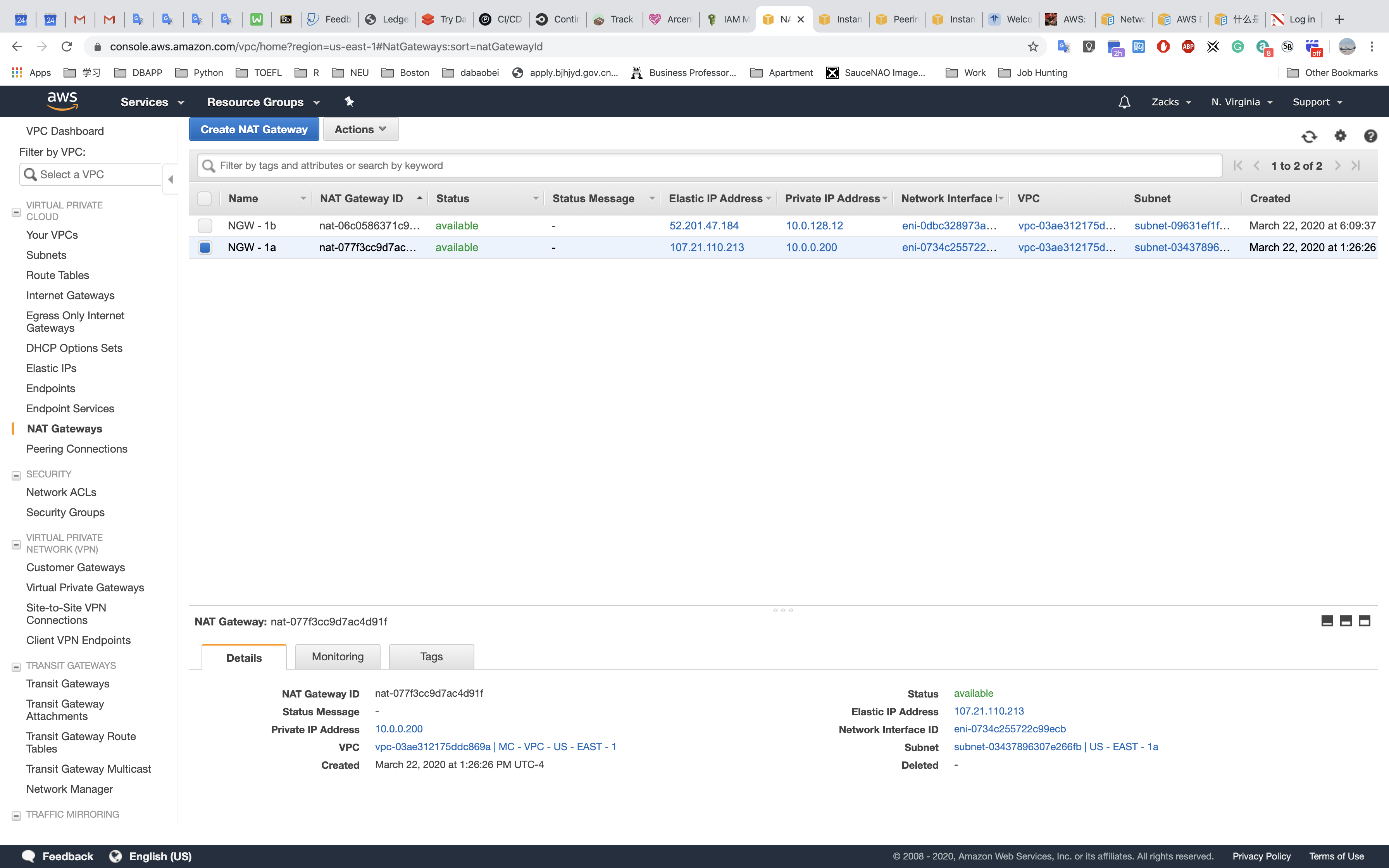
Route Tables
Public Route Table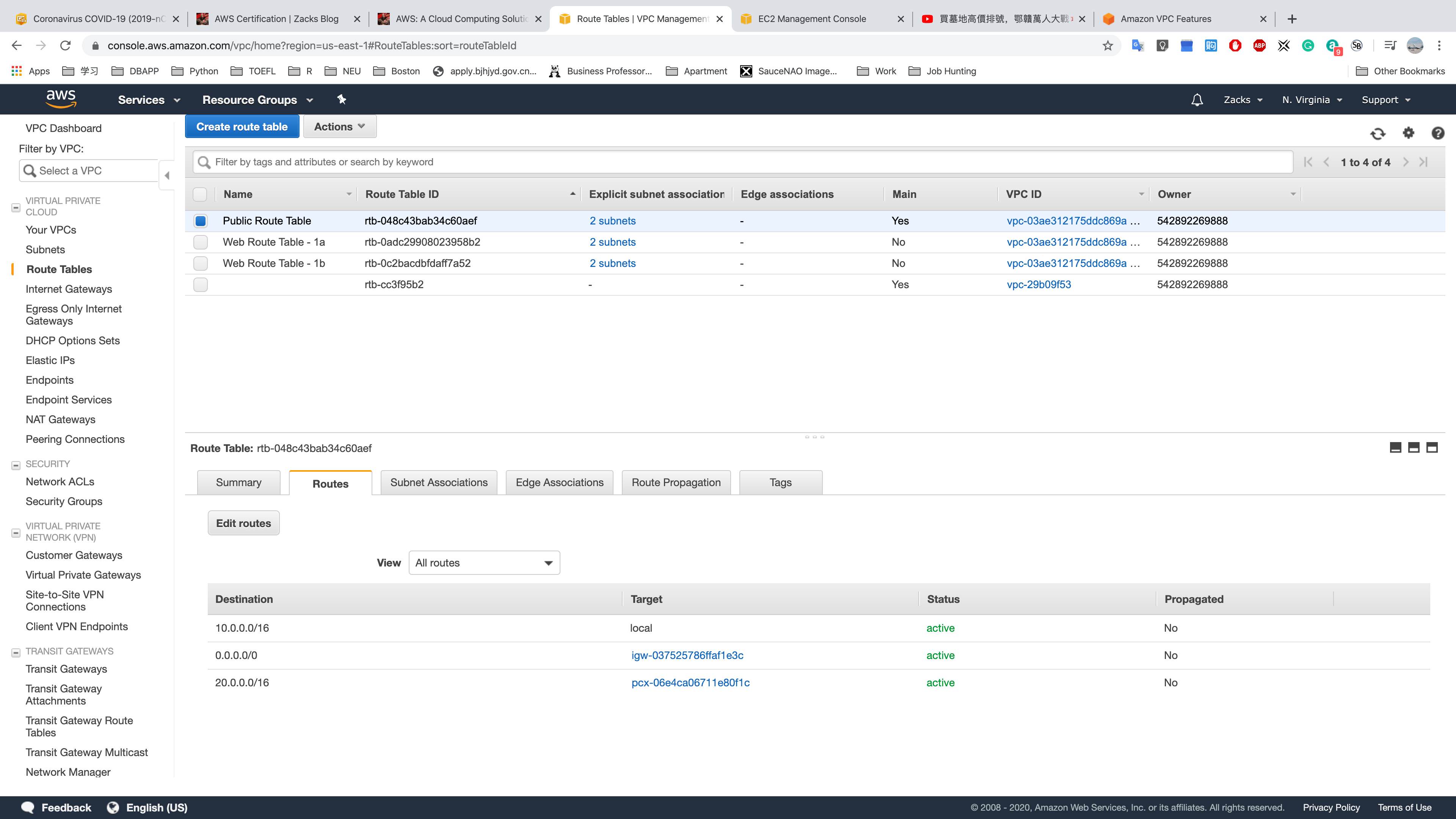
Web Route Table - 1a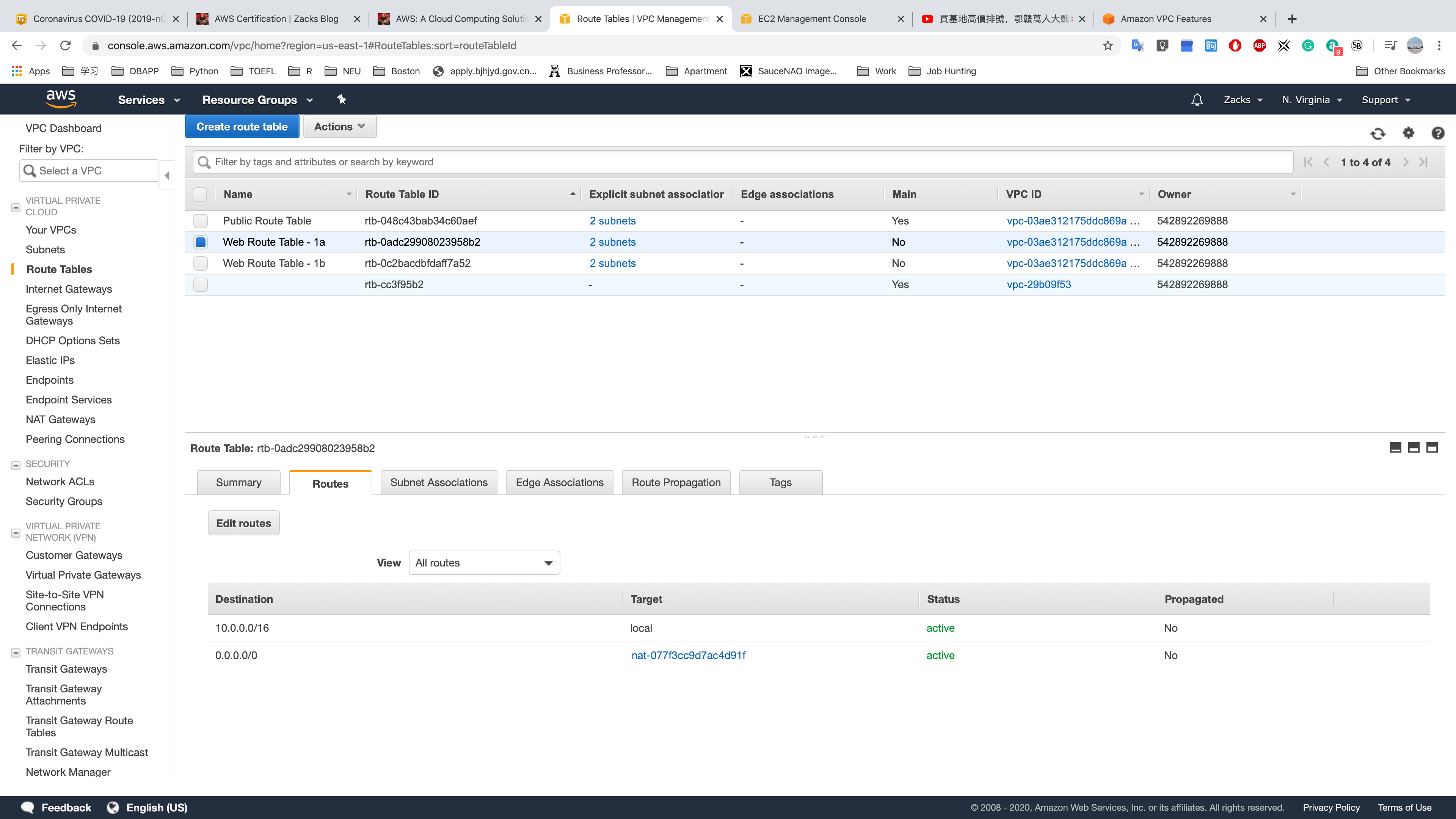
Web Route Table - 1b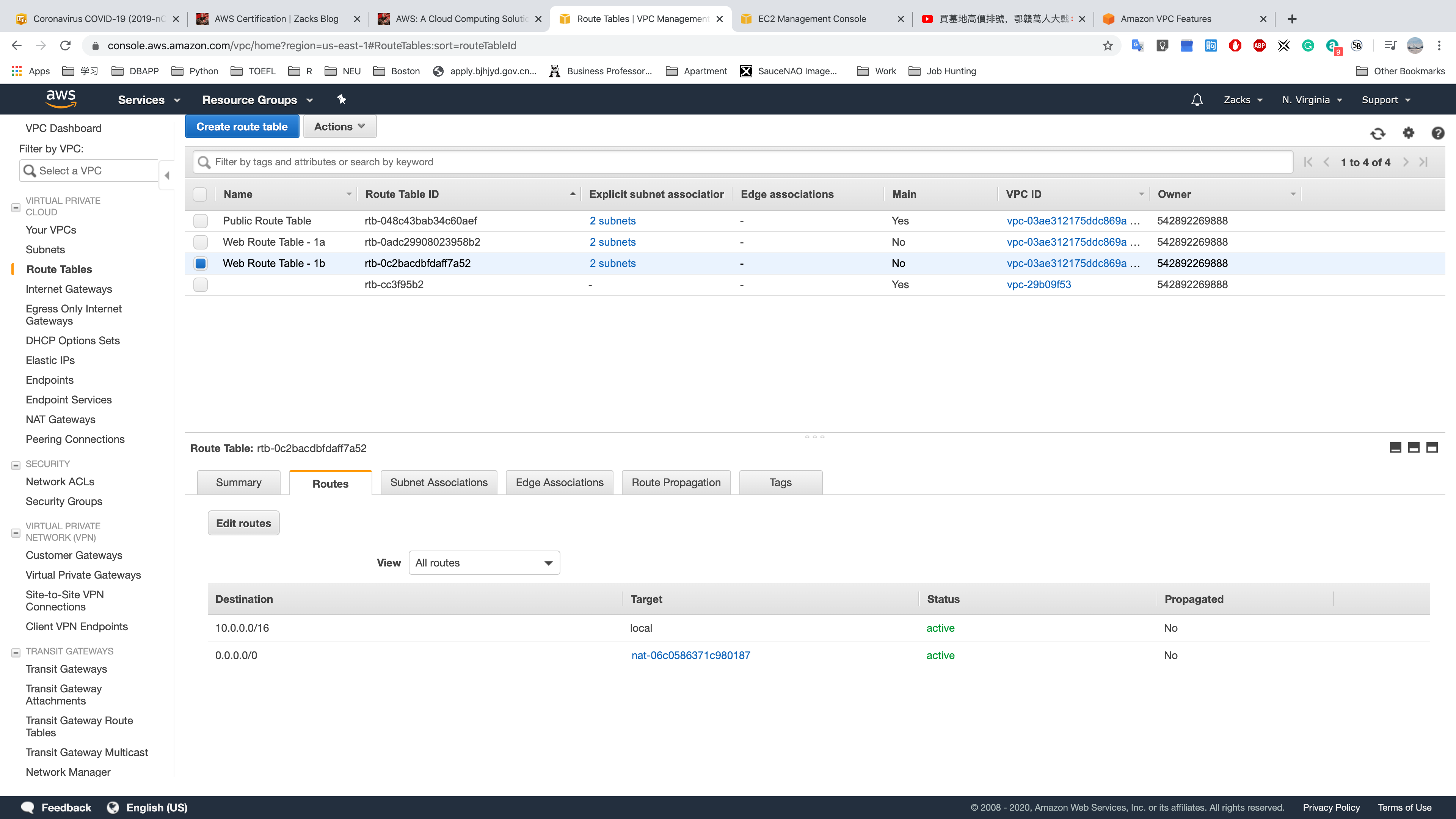
Security Groups
DB - for database: allowed all access from the U.S VPC and Europe VPC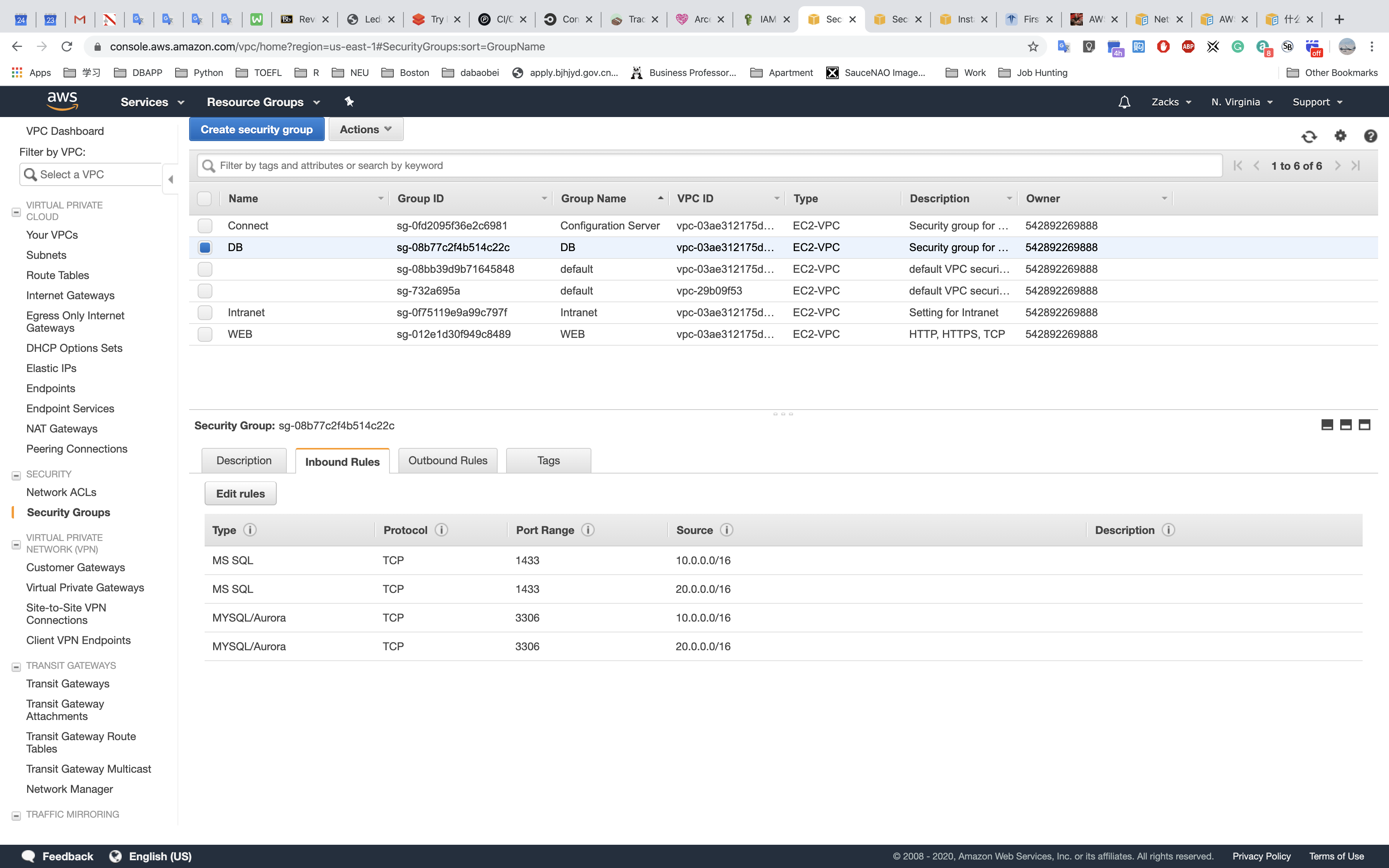
Connect - for connecting to the EC2 instances locate in public subnet)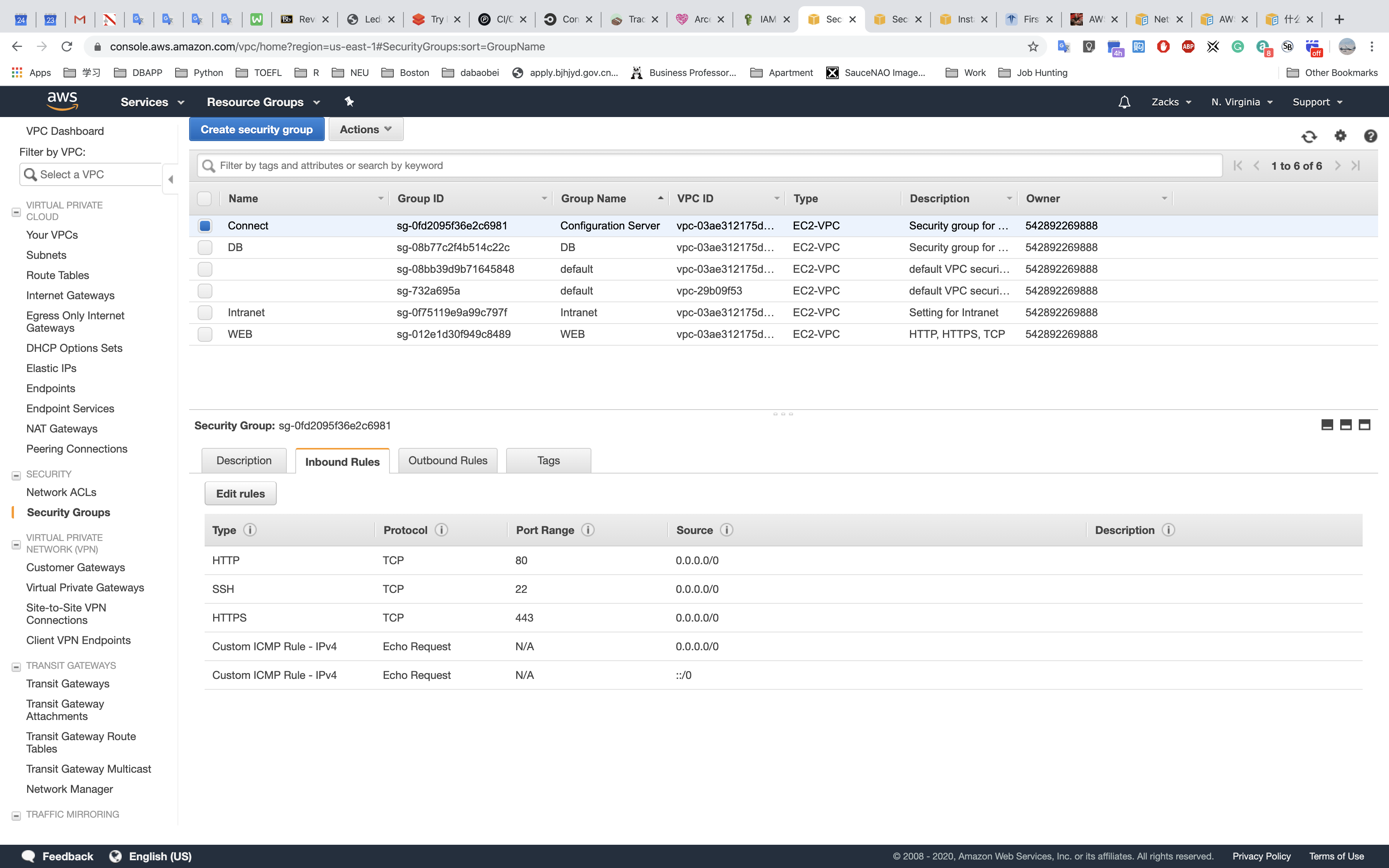
Intranet - for EC2 instances (Web Applications) that locate in the privates subnets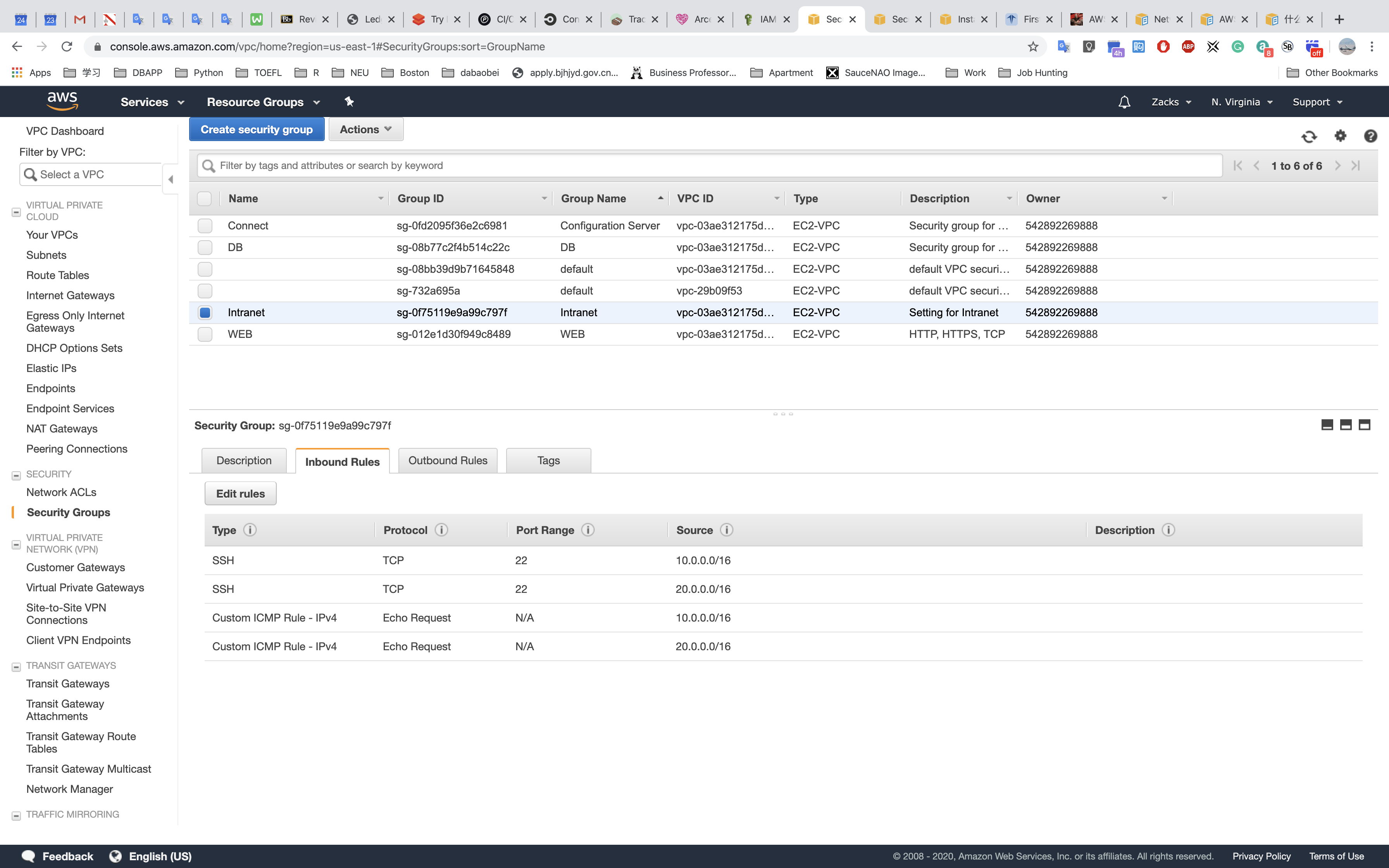
WEB - for EC2 instances (Web Applications) connecting to the Internet.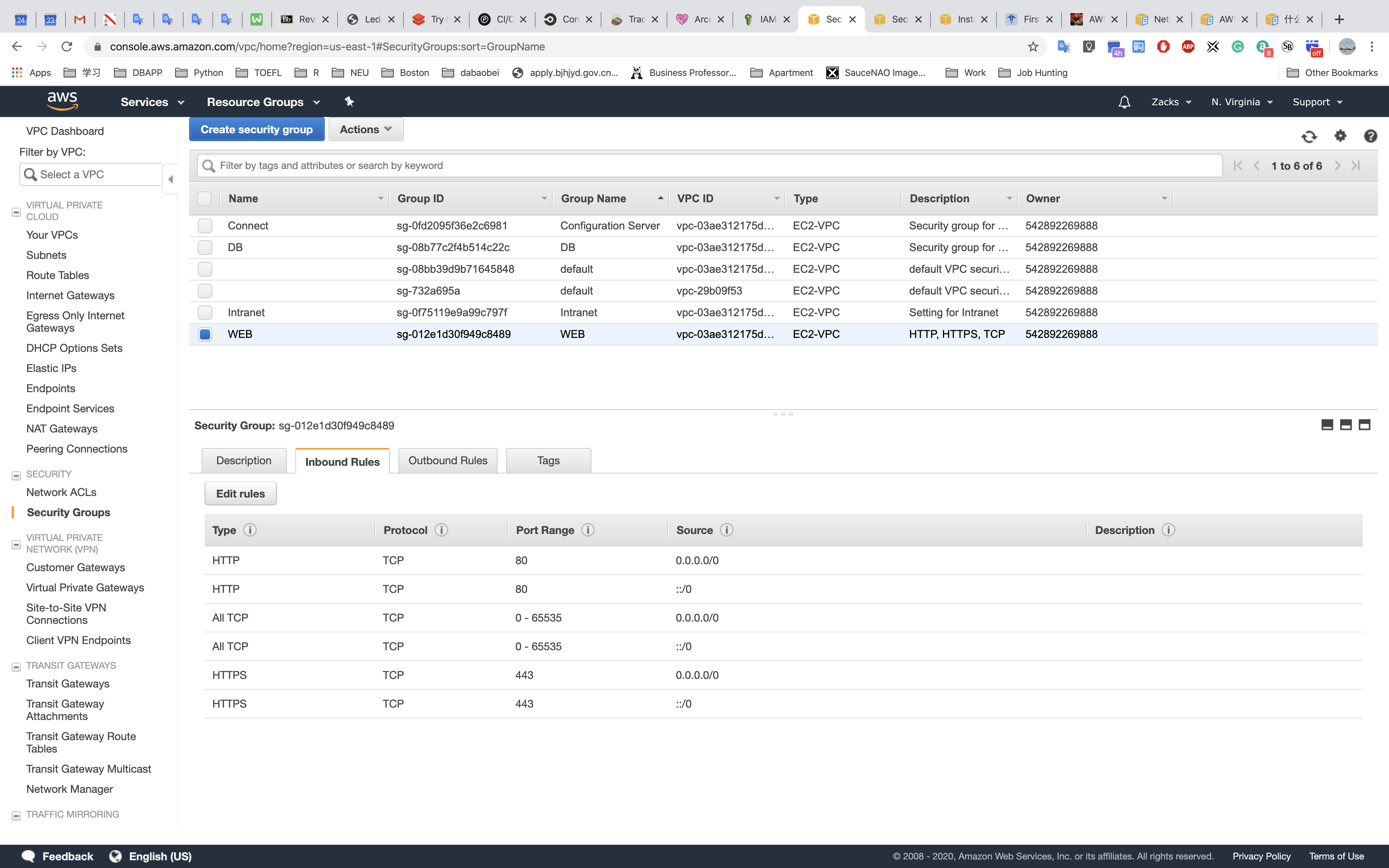
Peering Connection
Peering Connection is designed for building the connections among AWS VPCs.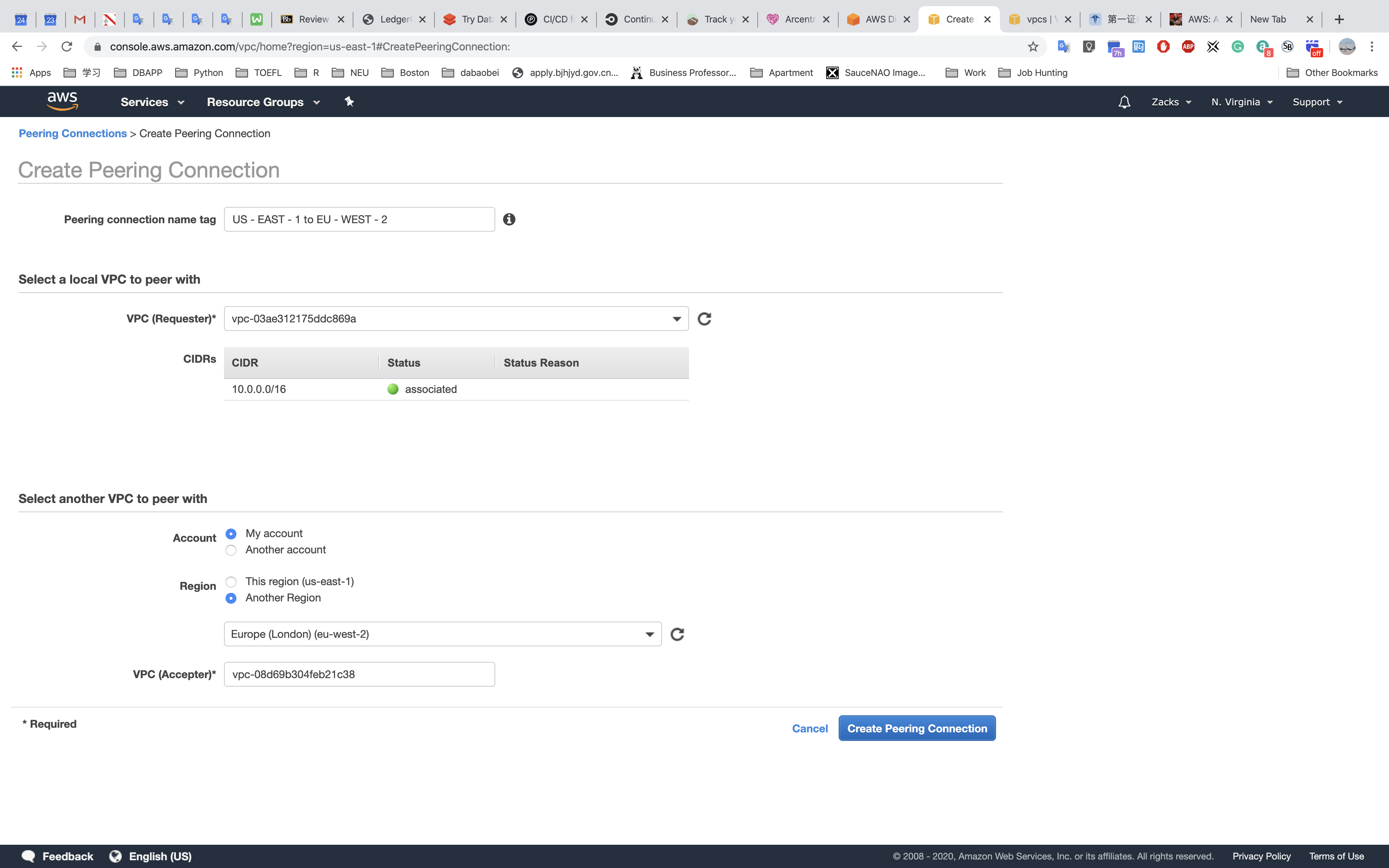
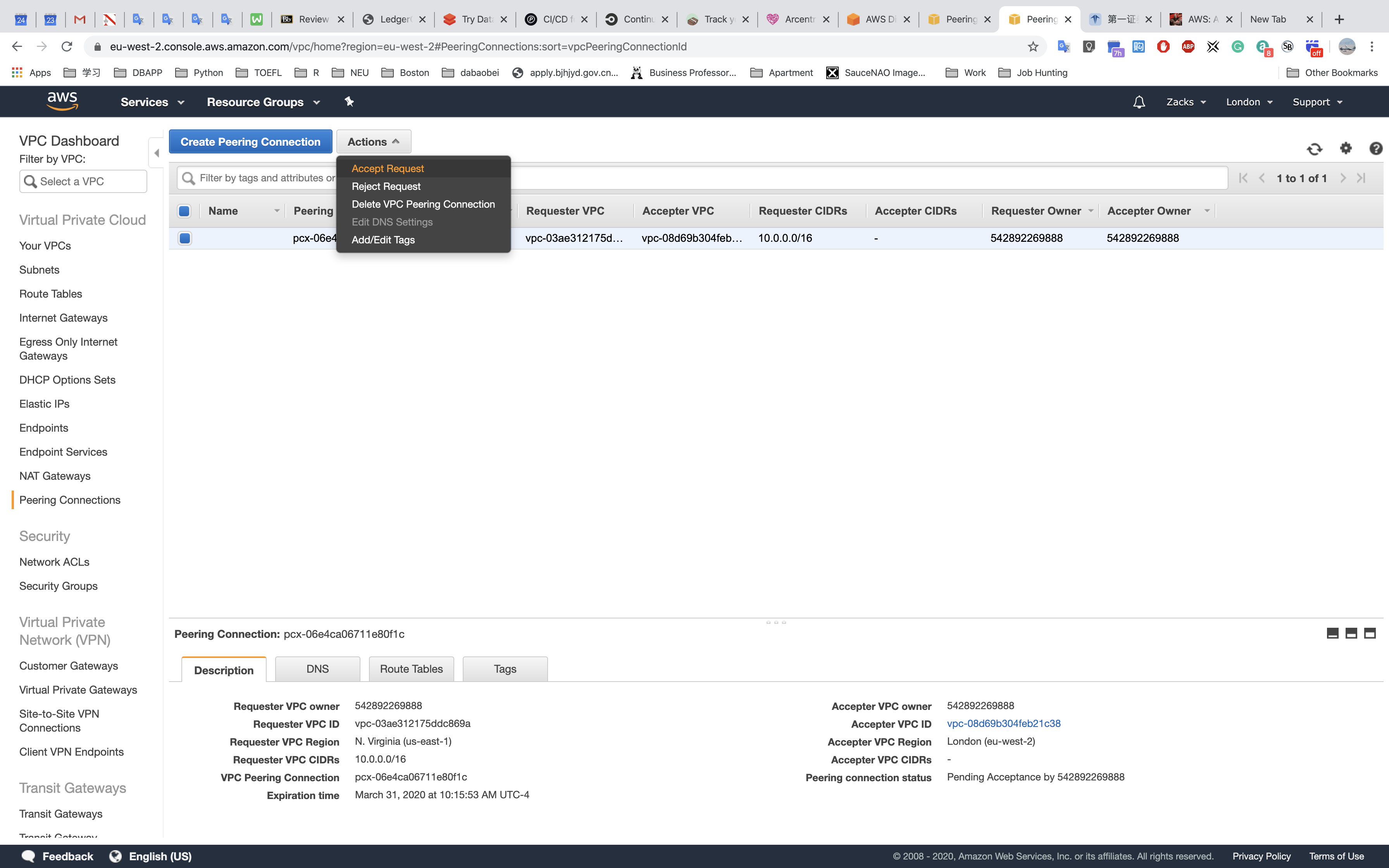
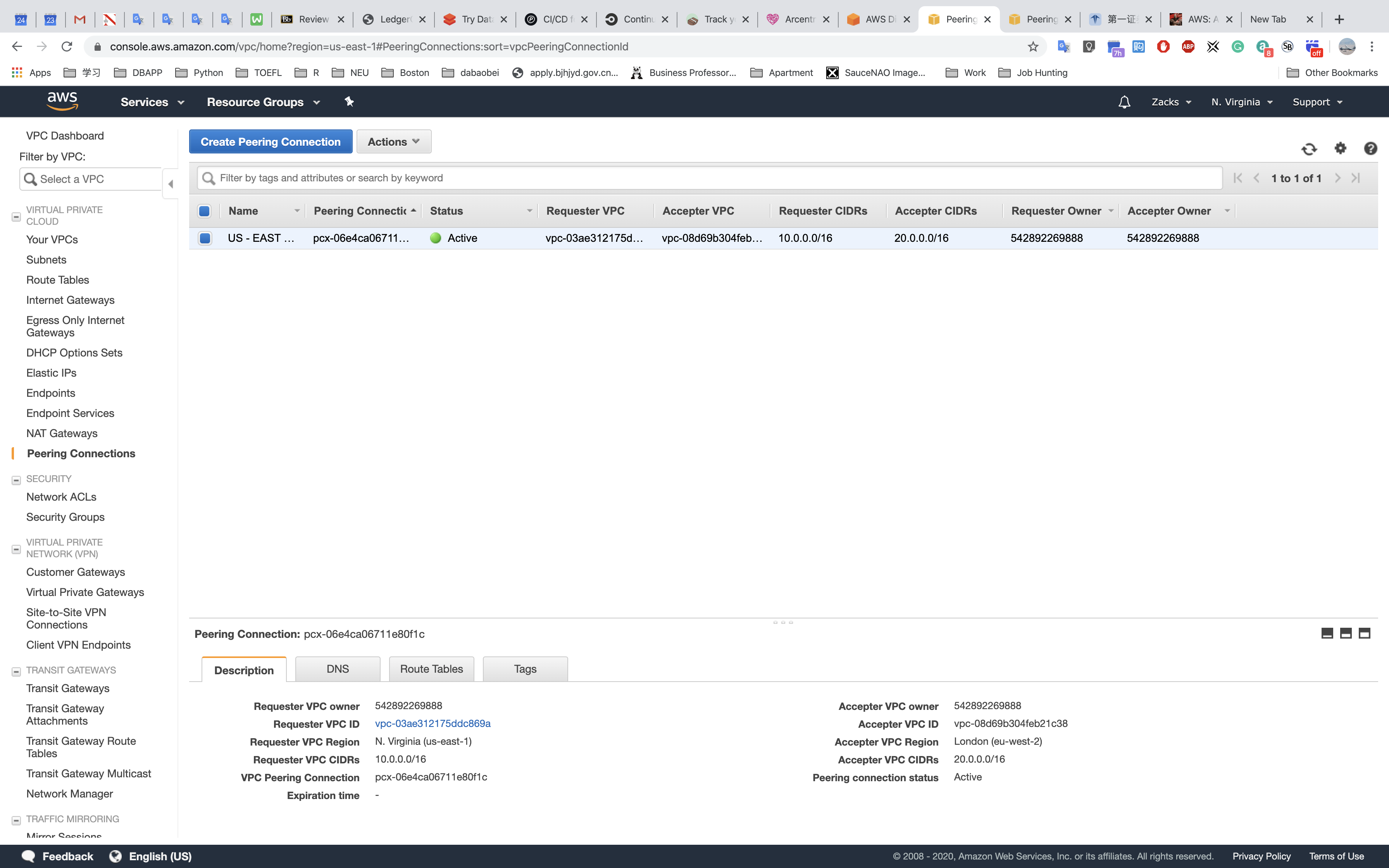
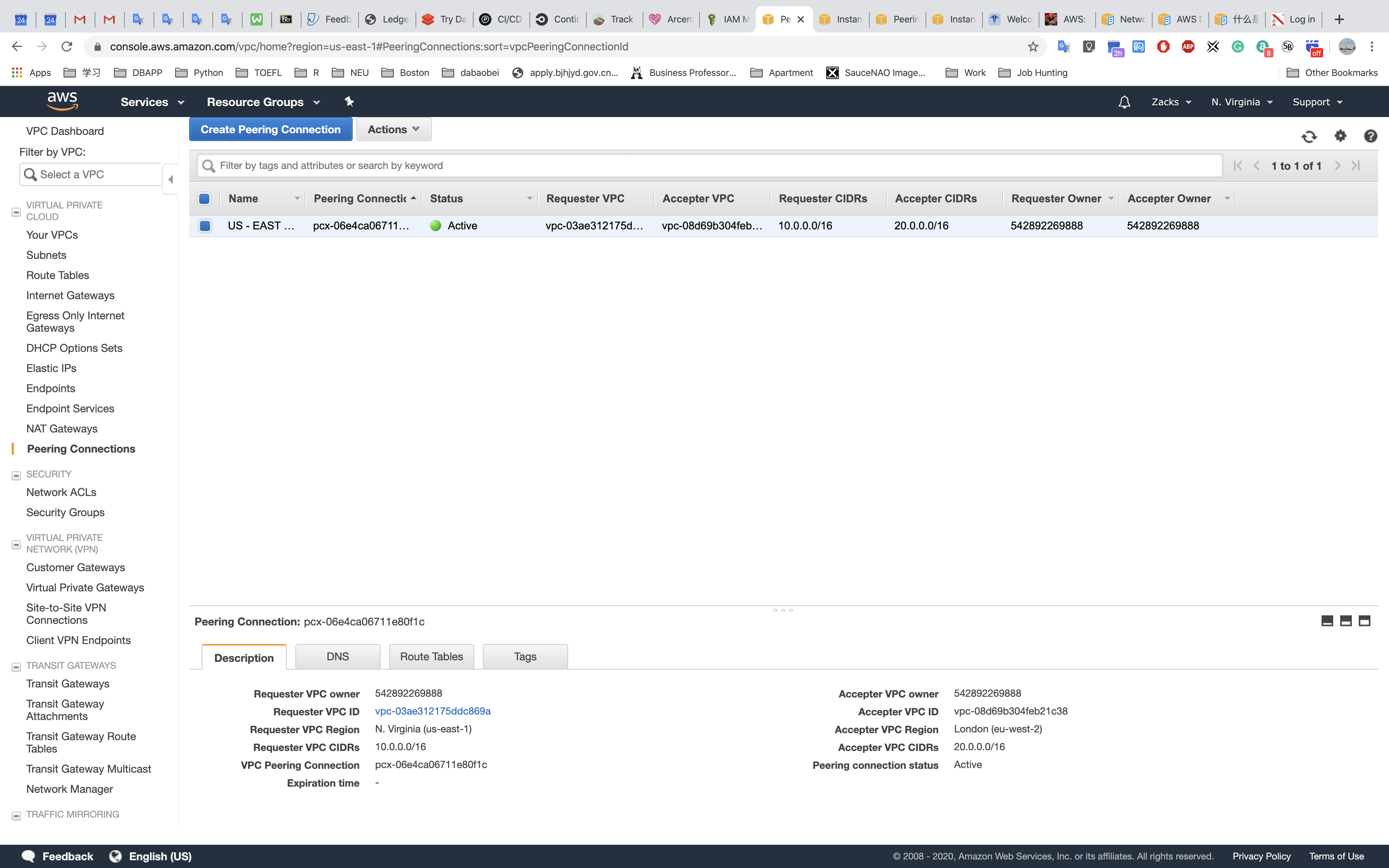
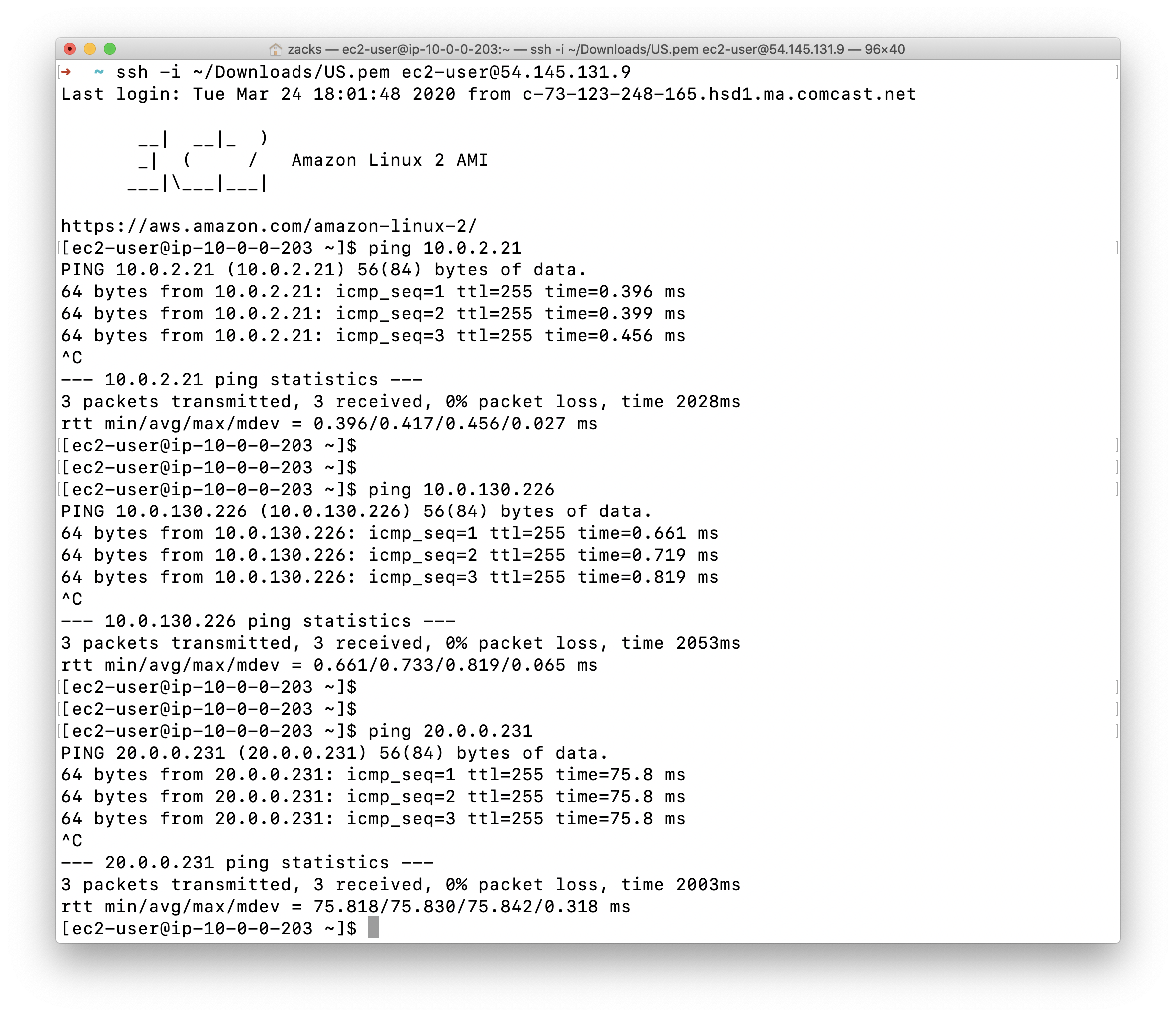
Connecting test
US - EAST - 1
1 | # Login to the Configuration Server in US - EAST - 1 |
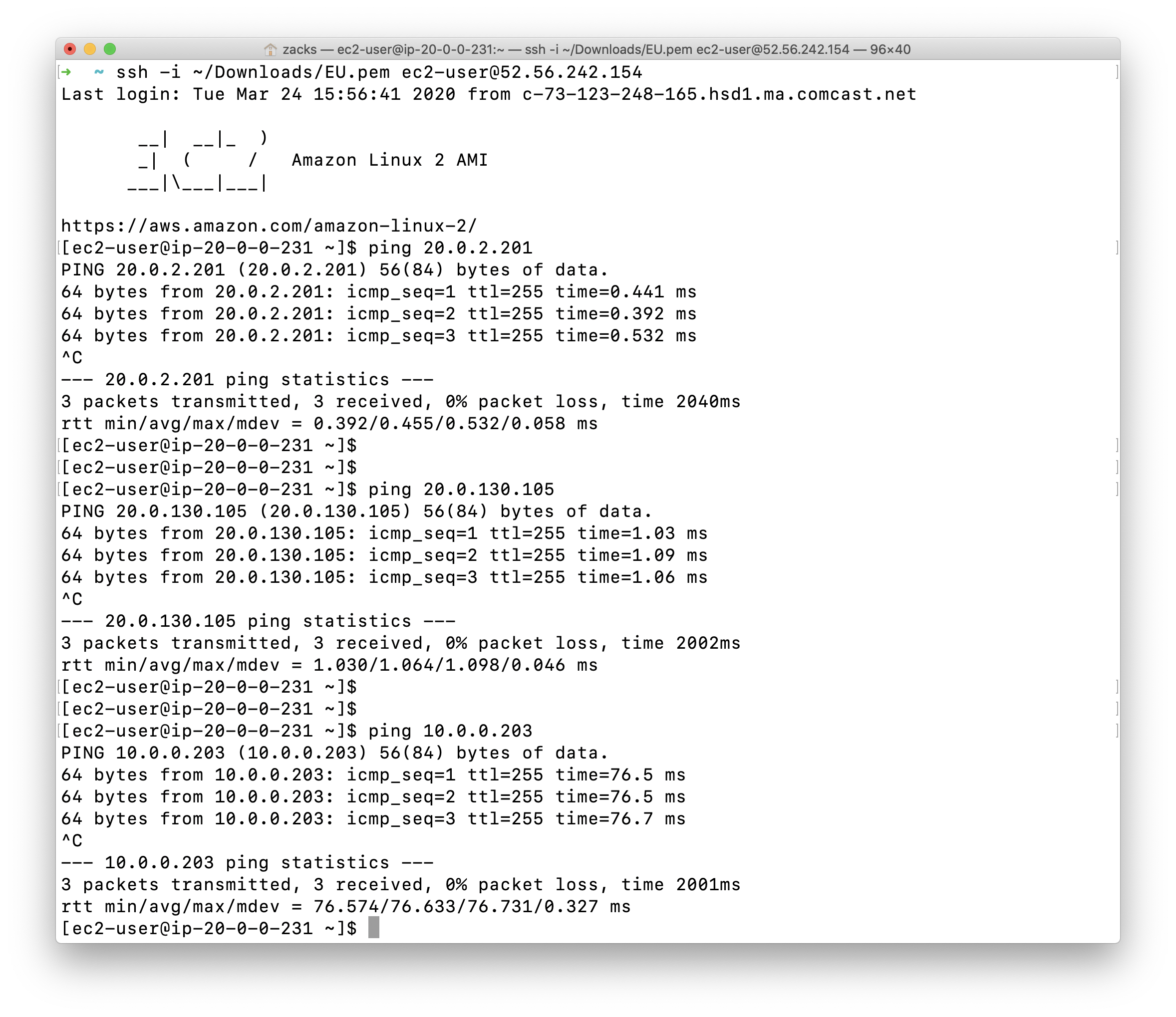
EU - WEST - 2
1 | # Login to the Configuration Server in EU - WEST - 2 |
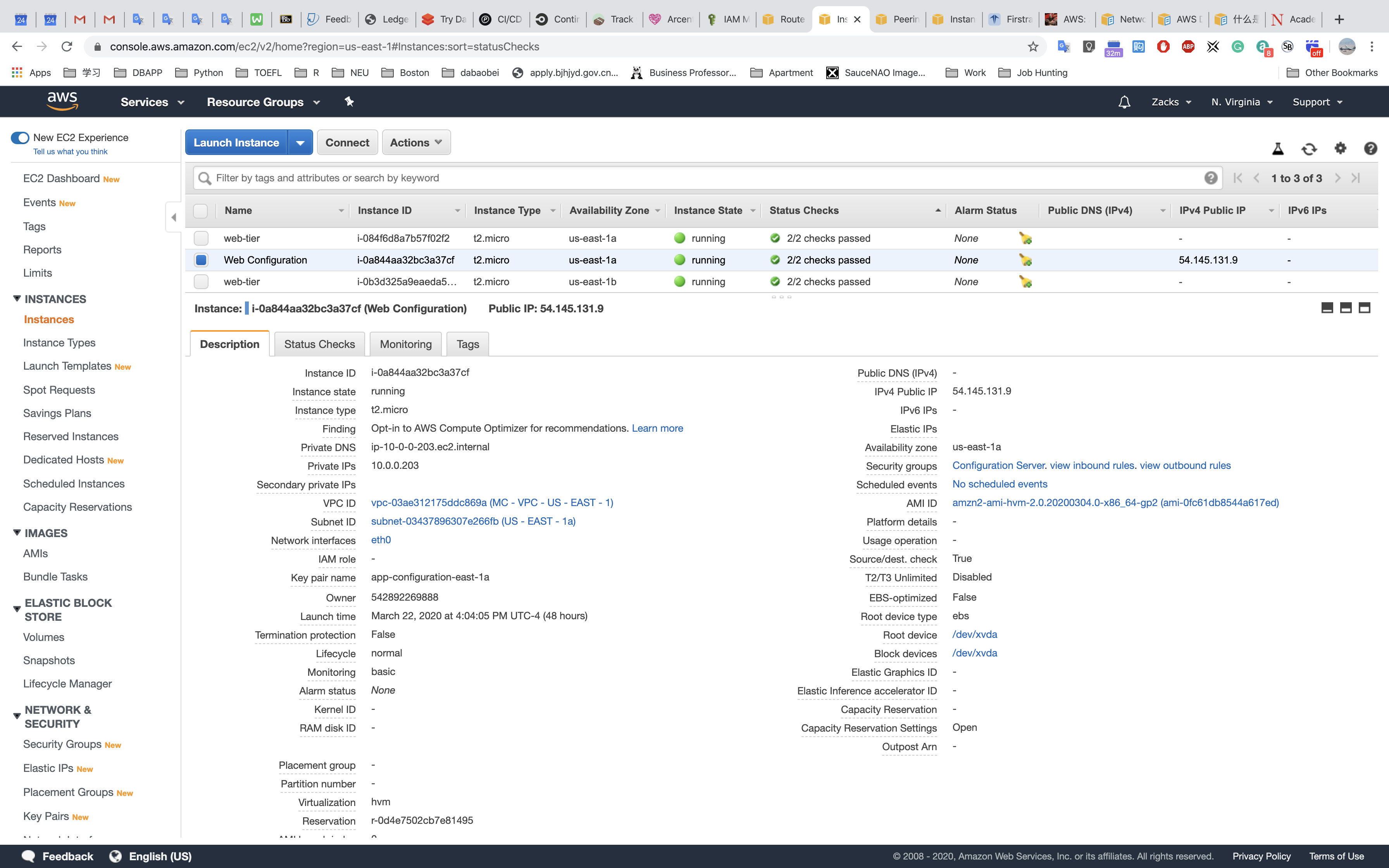
Web Configuration Settings:
Configuration Server
As I set server in the public subnet (US - EAST - 1a, or USE - EAST - 1b), it will automatically get a public IP address because of the Auto-assign setting above mentioned.
1 | sudo yum update -y |
AMIs
Build an AMI based on the configuration server.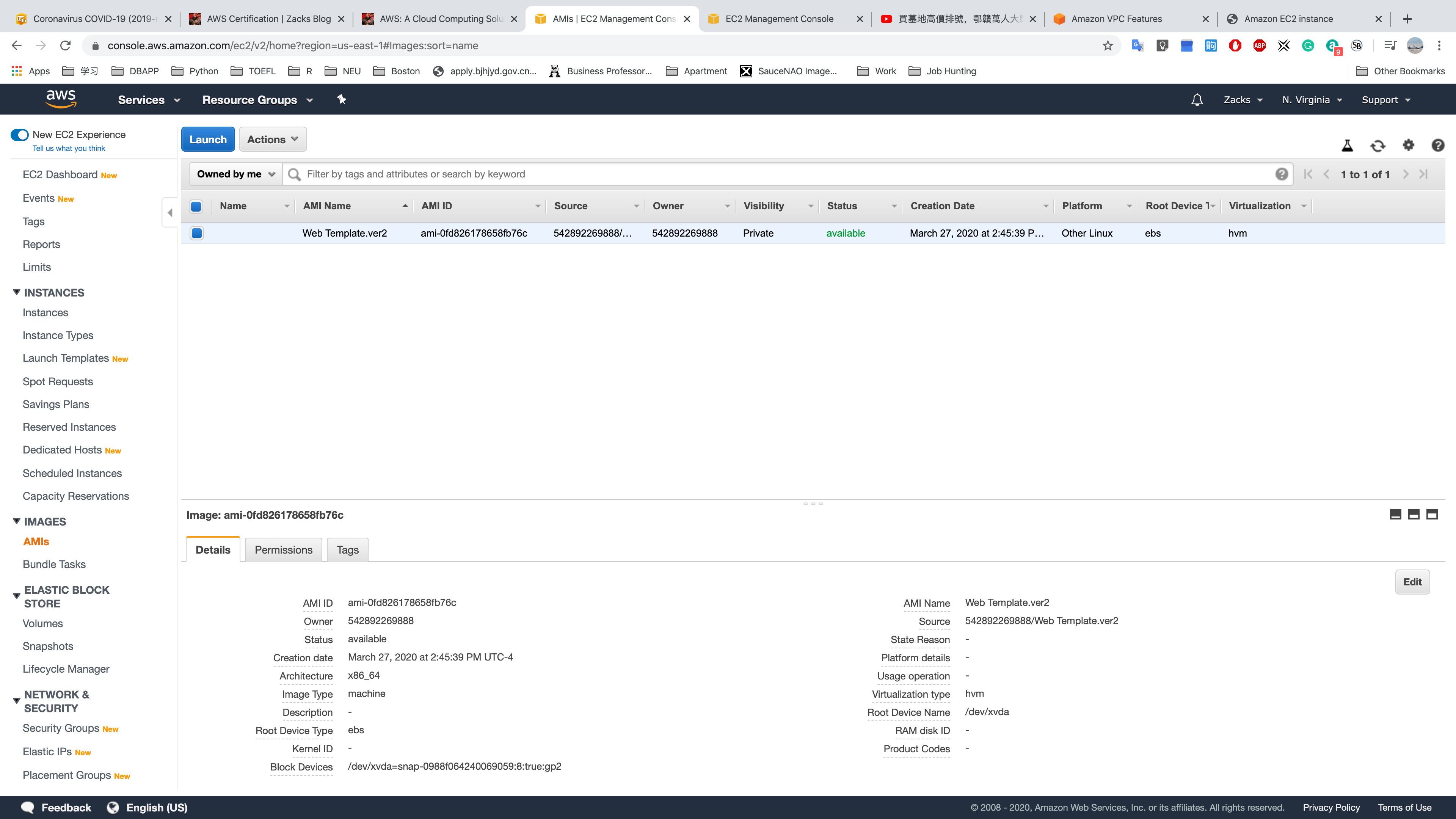
Load Balancer
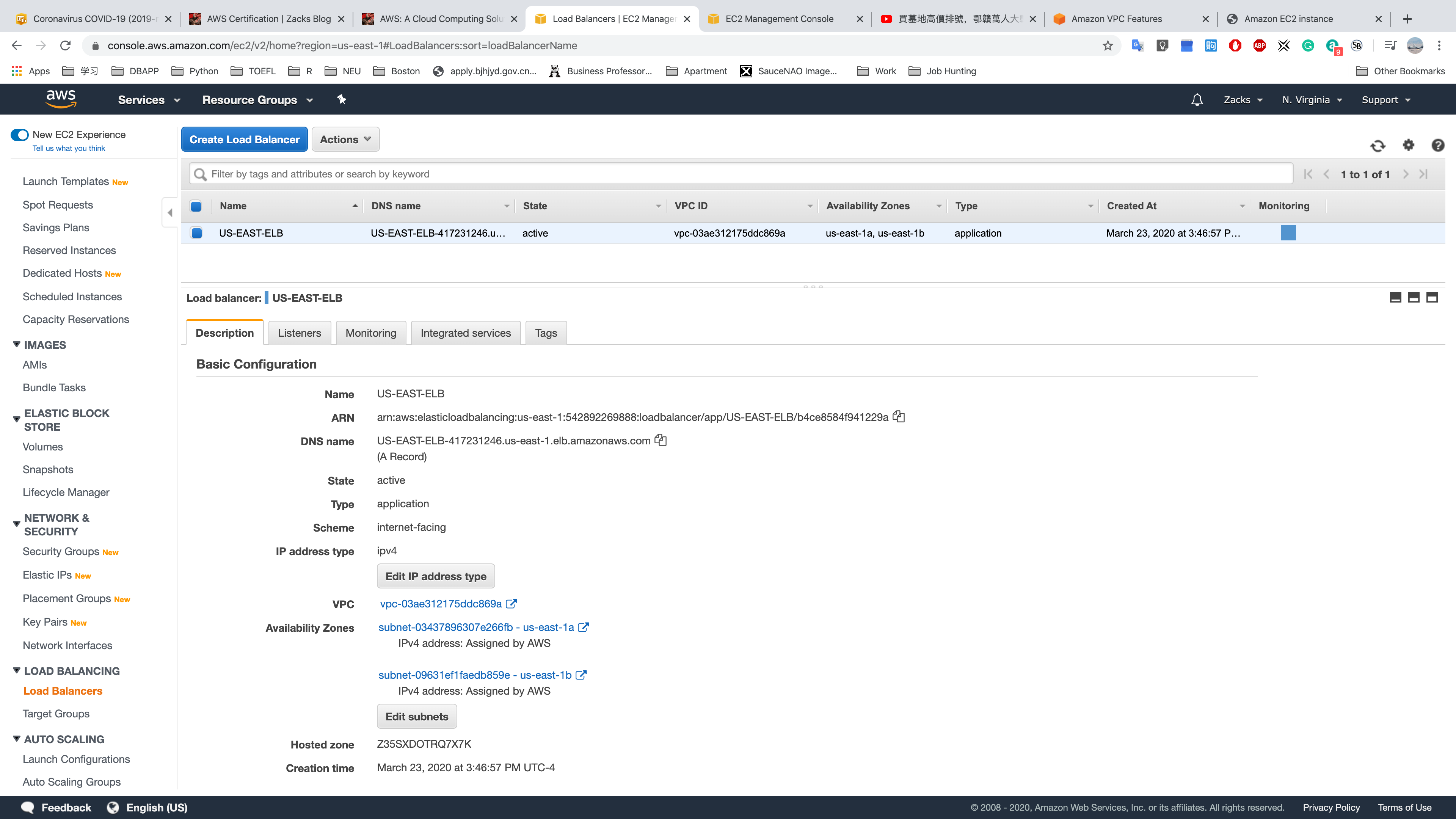
Load Balancing (AWS Elastic Load Balancing)
- Load Balancers
US-EAST-ELB: the ELB configuration template.
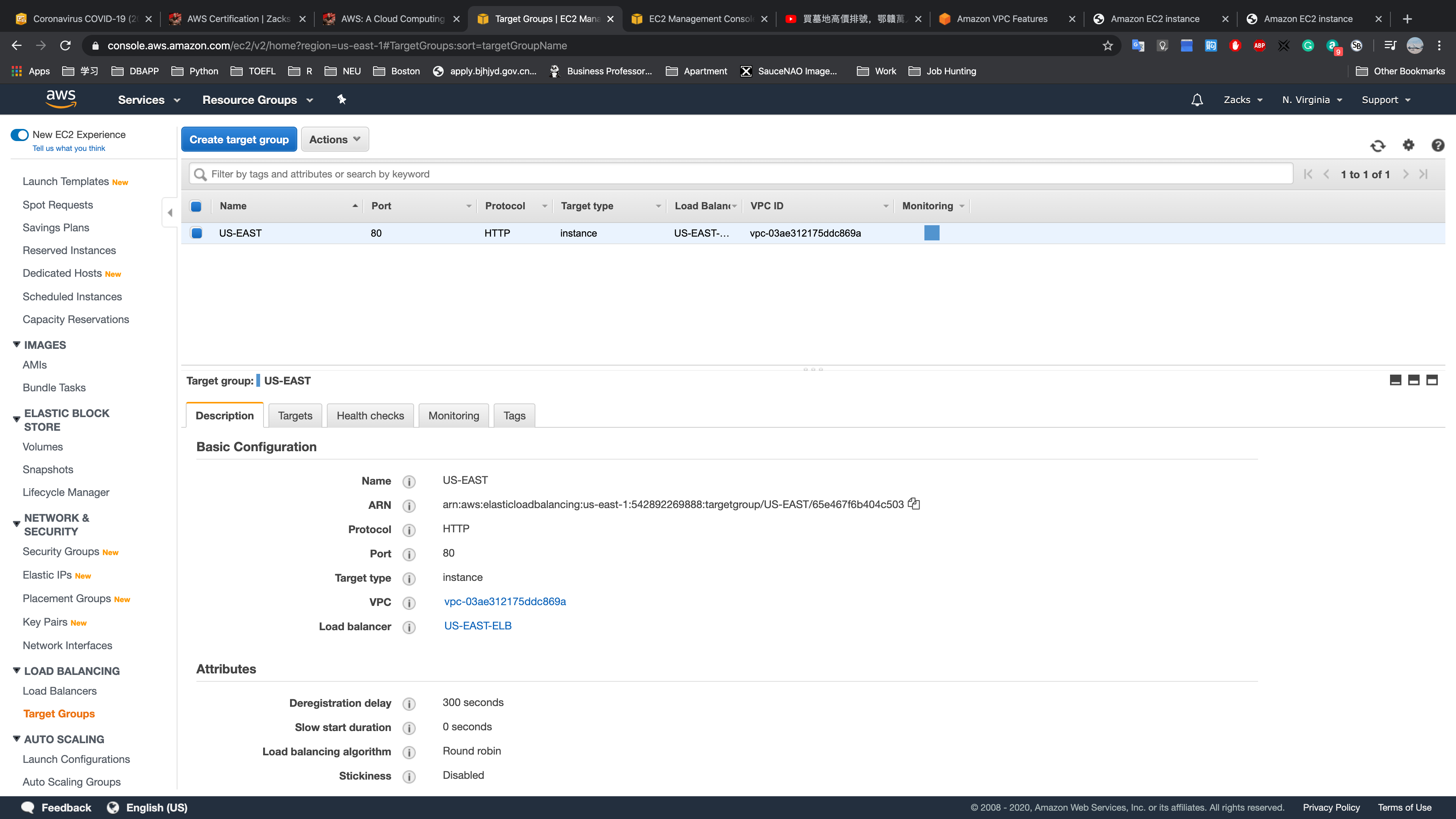
Load Balancing (AWS Elastic Load Balancing)
- Target Groups
US-EAST: define the groups that will apply the ELB configuration

Auto Scaling Groups
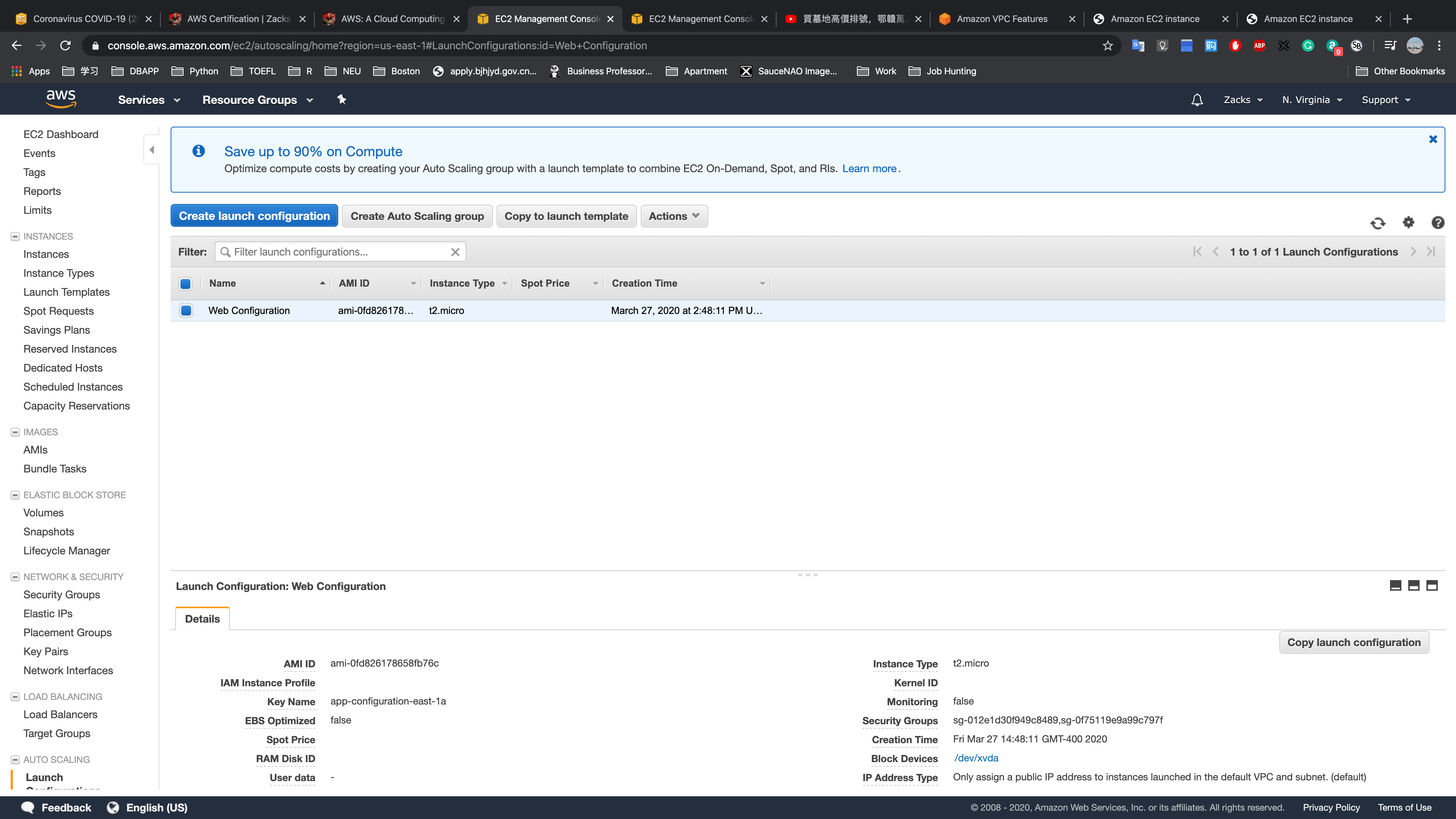
Auto Scaling:
- Launch Configurations
Web Configuration: the HA configuration template.
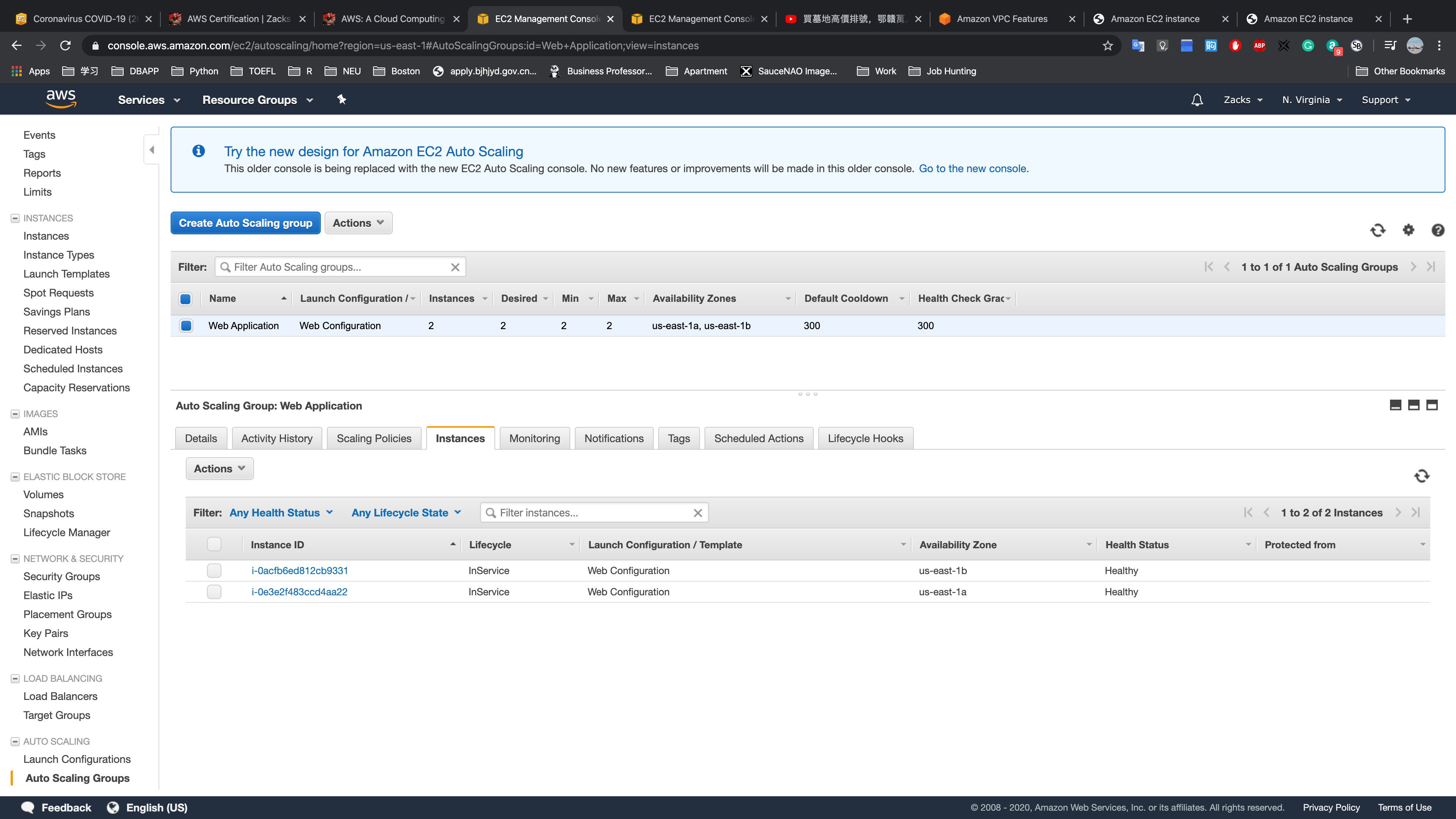
Auto Scaling:
- Auto Scaling Groups:
Web Application: define the groups that will apply the HA configuration template.
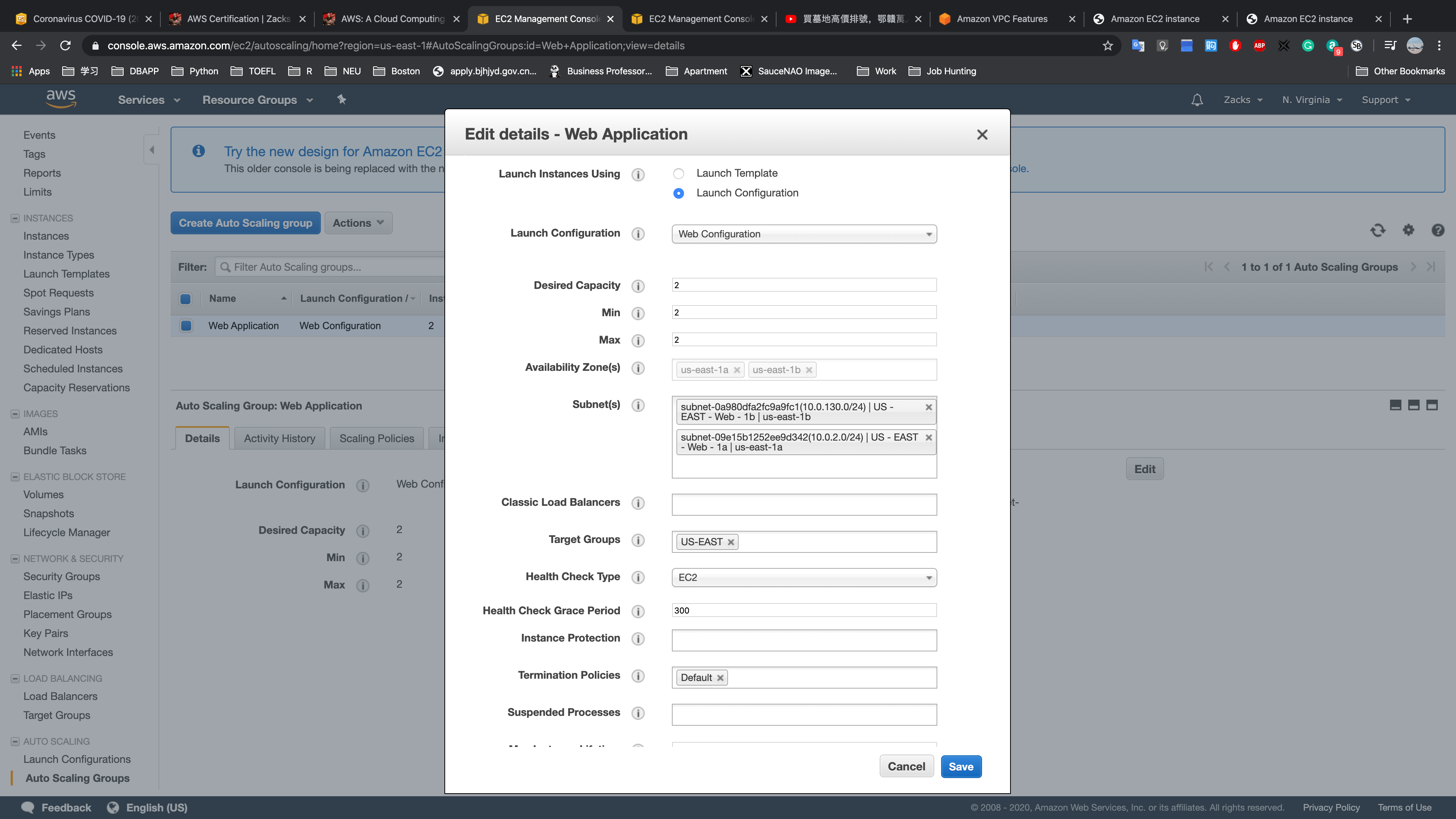
Target Groups is the crucial setting for working with ELB.
RDS
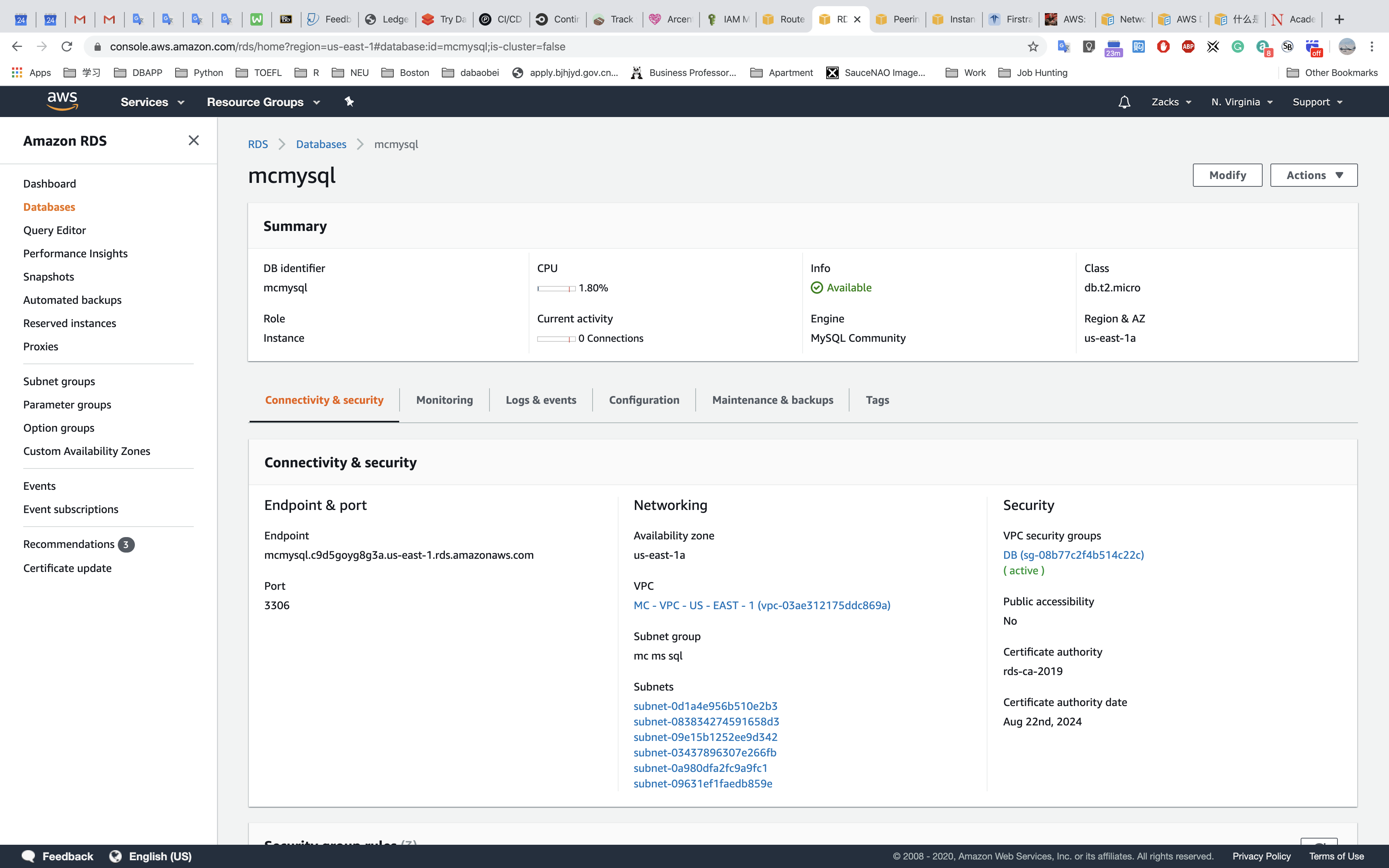
Test connectivity of RDS through US - EAST - 1 private subnet.
- Login the configuration server:
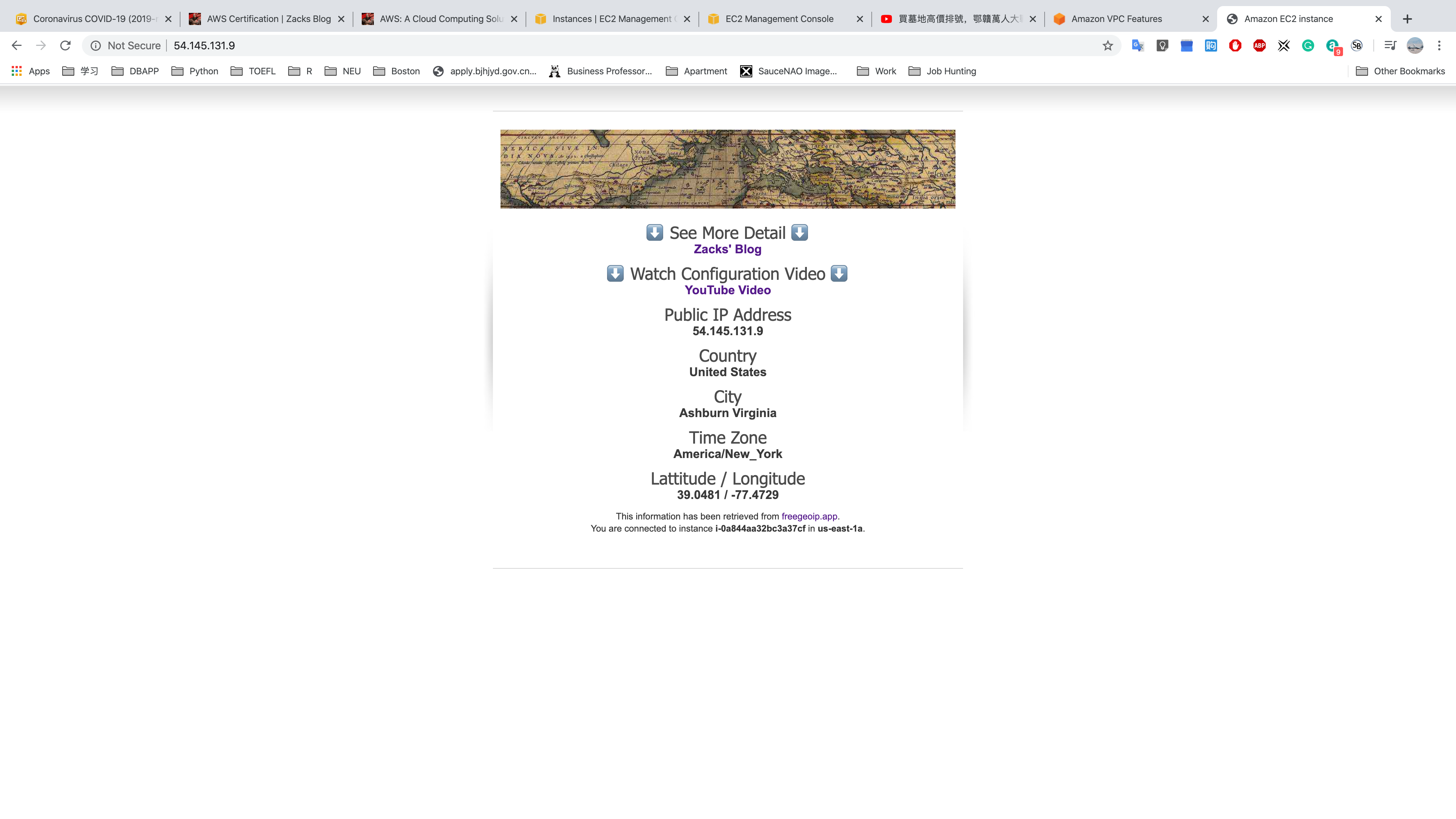
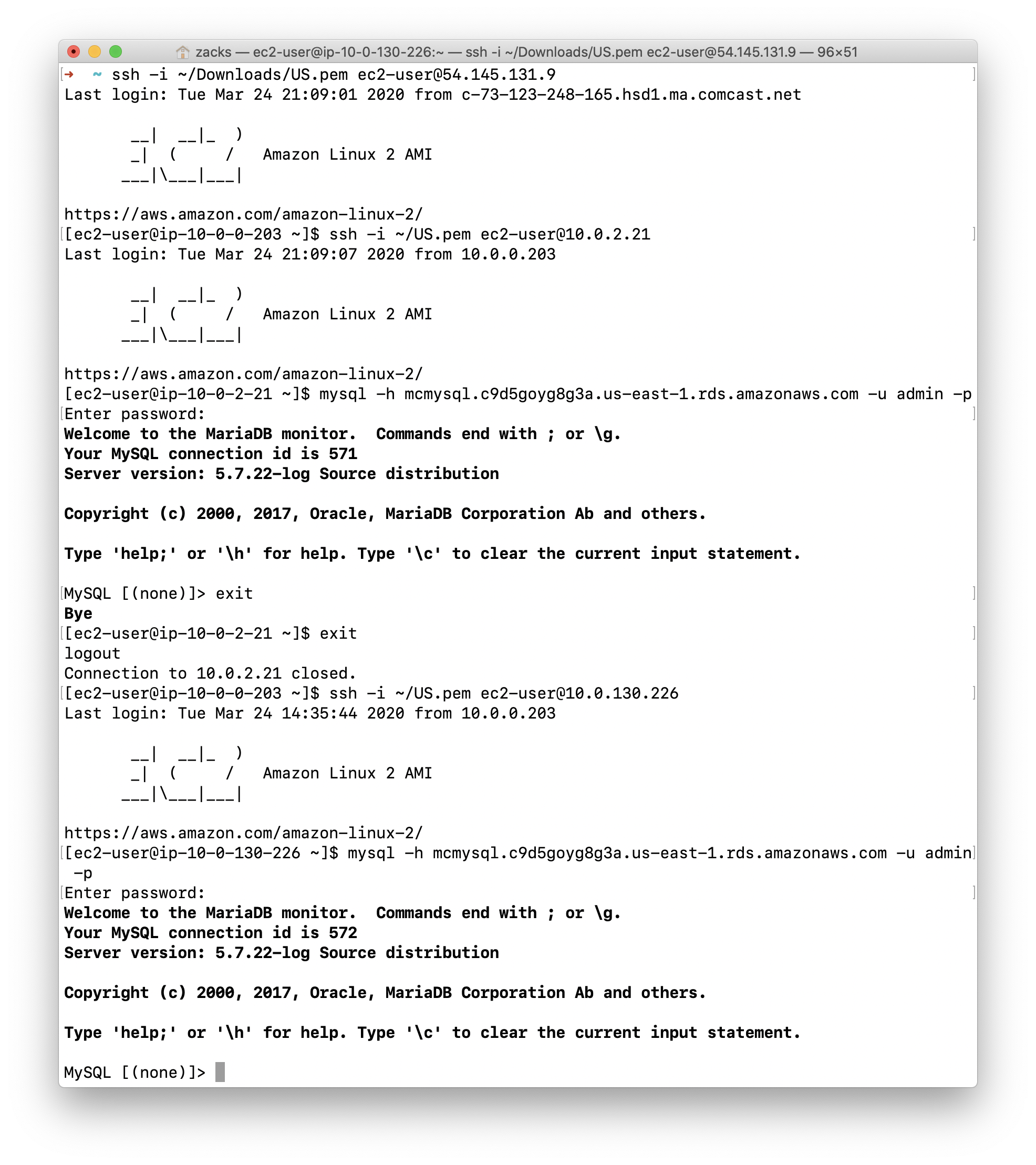
ssh -i ~/Downloads/US.pem ec2-user@54.145.131.9 - Login one of the server in private subnet:
ssh -i ~/US.pem ec2-user@10.0.2.21 - Test connectivity of RDS:
mysql -h mcmysql.c9d5goyg8g3a.us-east-1.rds.amazonaws.com -u admin -p - Exit the SQL:
exit - Return to the configuration server:
exit - Login the server in the other private subnet:
ssh -i ~/US.pem ec2-user@10.0.130.226 - Test connectivity of RDS:
mysql -h mcmysql.c9d5goyg8g3a.us-east-1.rds.amazonaws.com -u admin -p
Test connectivity of RDS through EU - WEST - 2 private subnet.
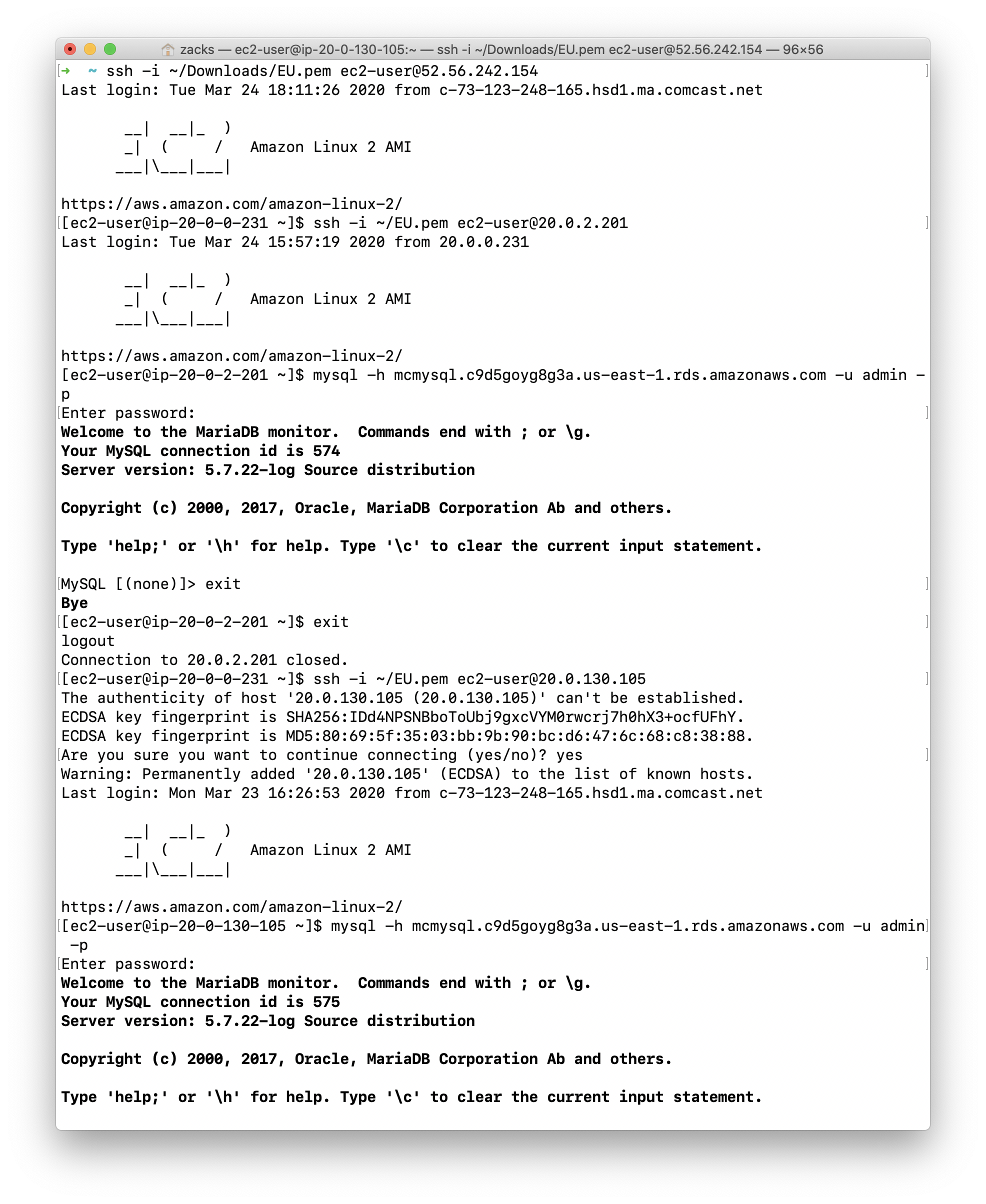
- Login the configuration server:
ssh -i ~/Downloads/EU.pem ec2-user@52.56.242.154 - Login one of the server in private subnet:
ssh -i ~/EU.pem ec2-user@20.0.2.201 - Test connectivity of RDS:
mysql -h mcmysql.c9d5goyg8g3a.us-east-1.rds.amazonaws.com -u admin -p - Exit the SQL:
exit - Return to the configuration server:
exit - Login the server in the other private subnet:
ssh -i ~/EU.pem ec2-user@20.0.130.105 - Test connectivity of RDS:
mysql -h mcmysql.c9d5goyg8g3a.us-east-1.rds.amazonaws.com -u admin -p
Route 53
DNS Settings
Two ways to create a route set in Route 53
Alias - No& Select an AWSAlias Target(could be your ELB) from the list.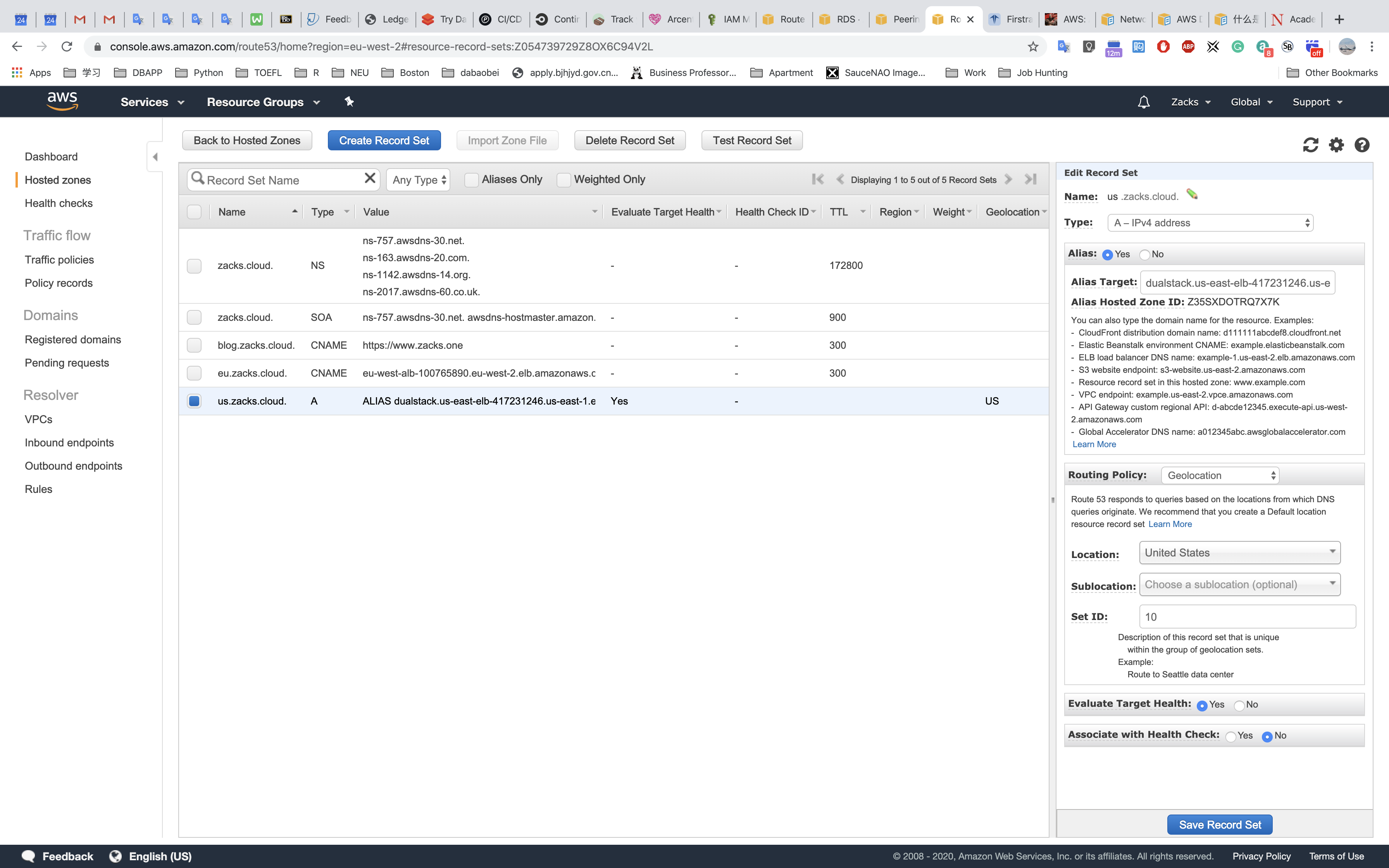
Alias - No& SetValue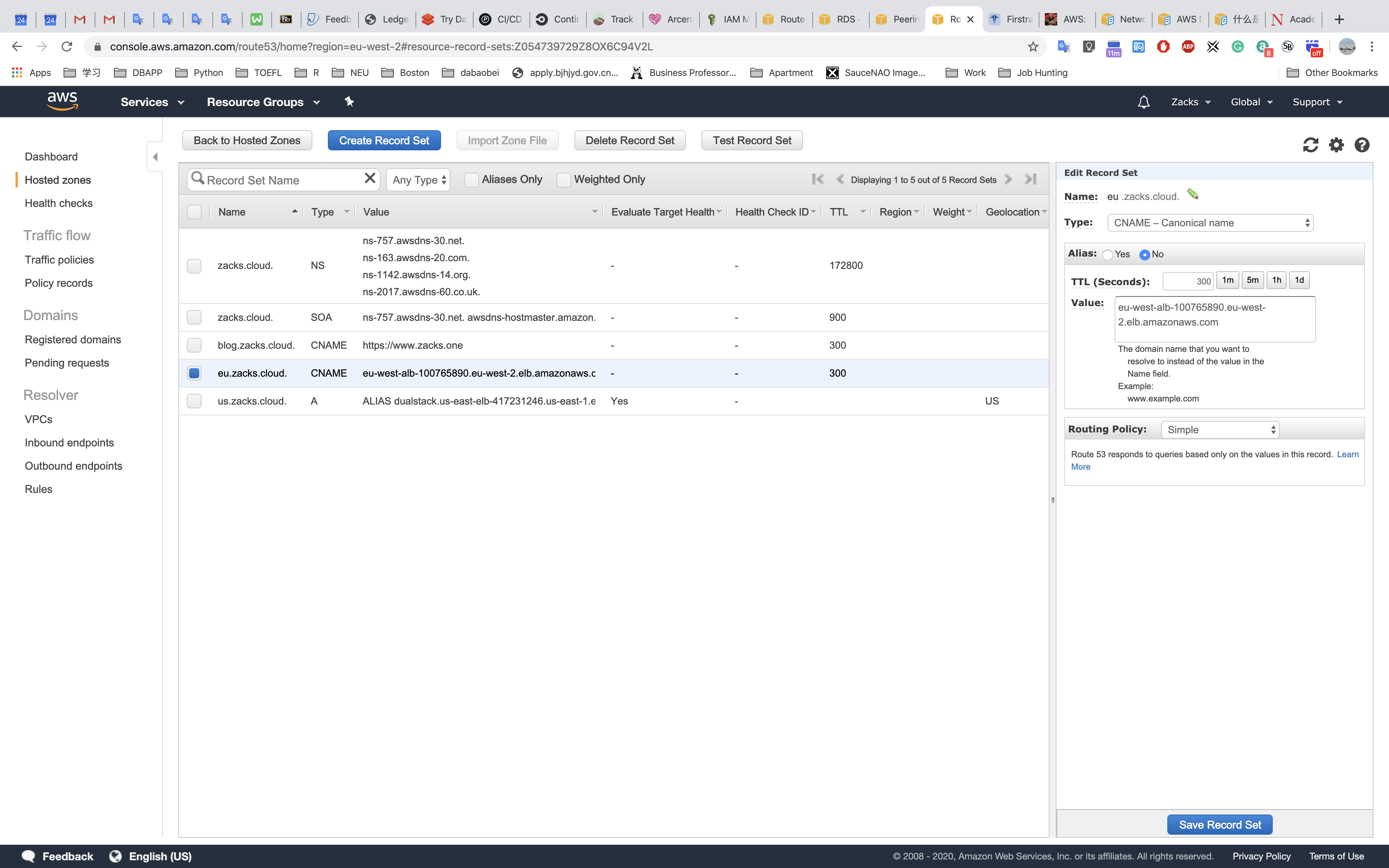
Testing ELB
US - EAST - 1 (us.zacks.cloud)

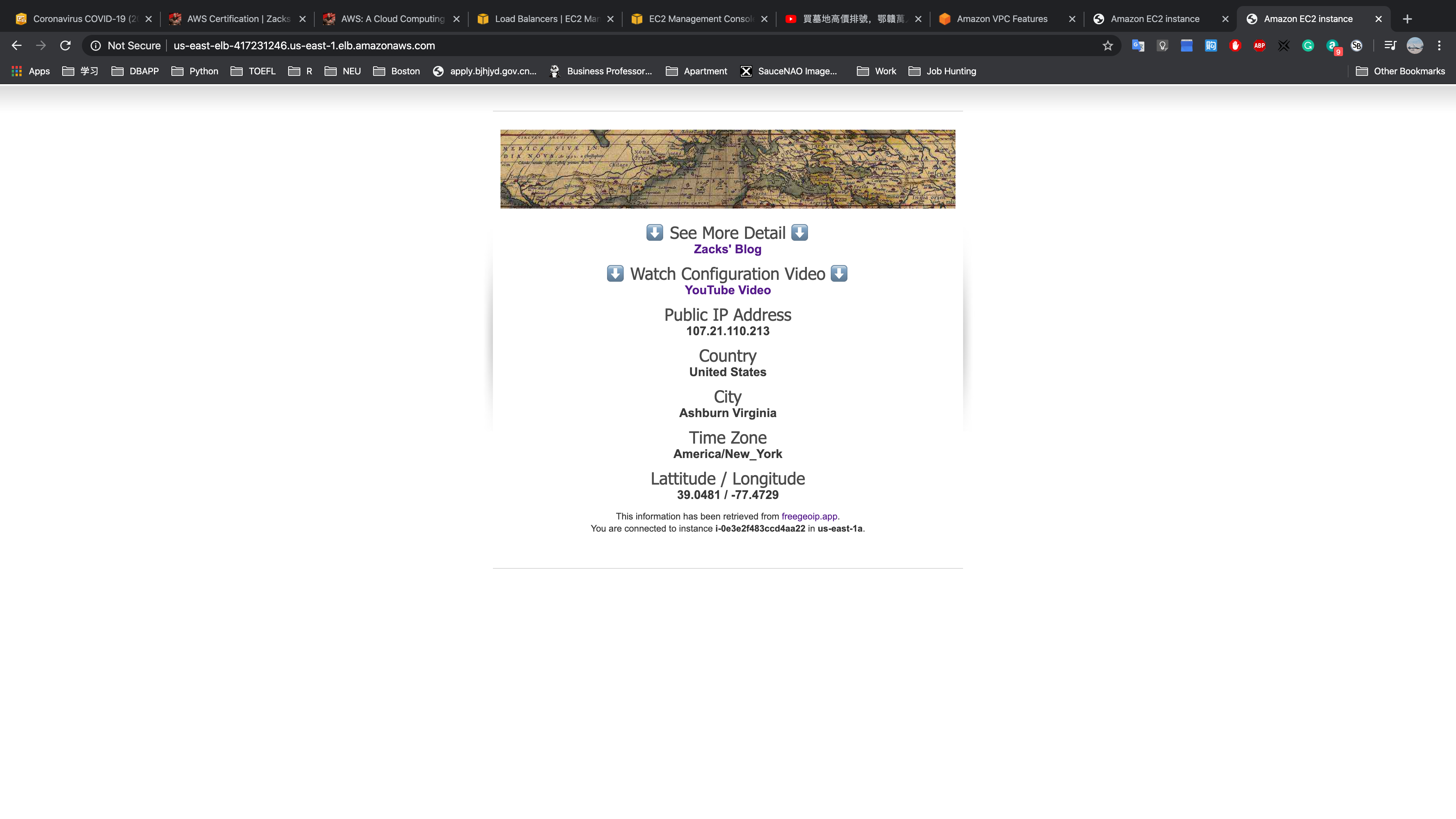
EU - WEST - 2 (us.zacks.cloud)
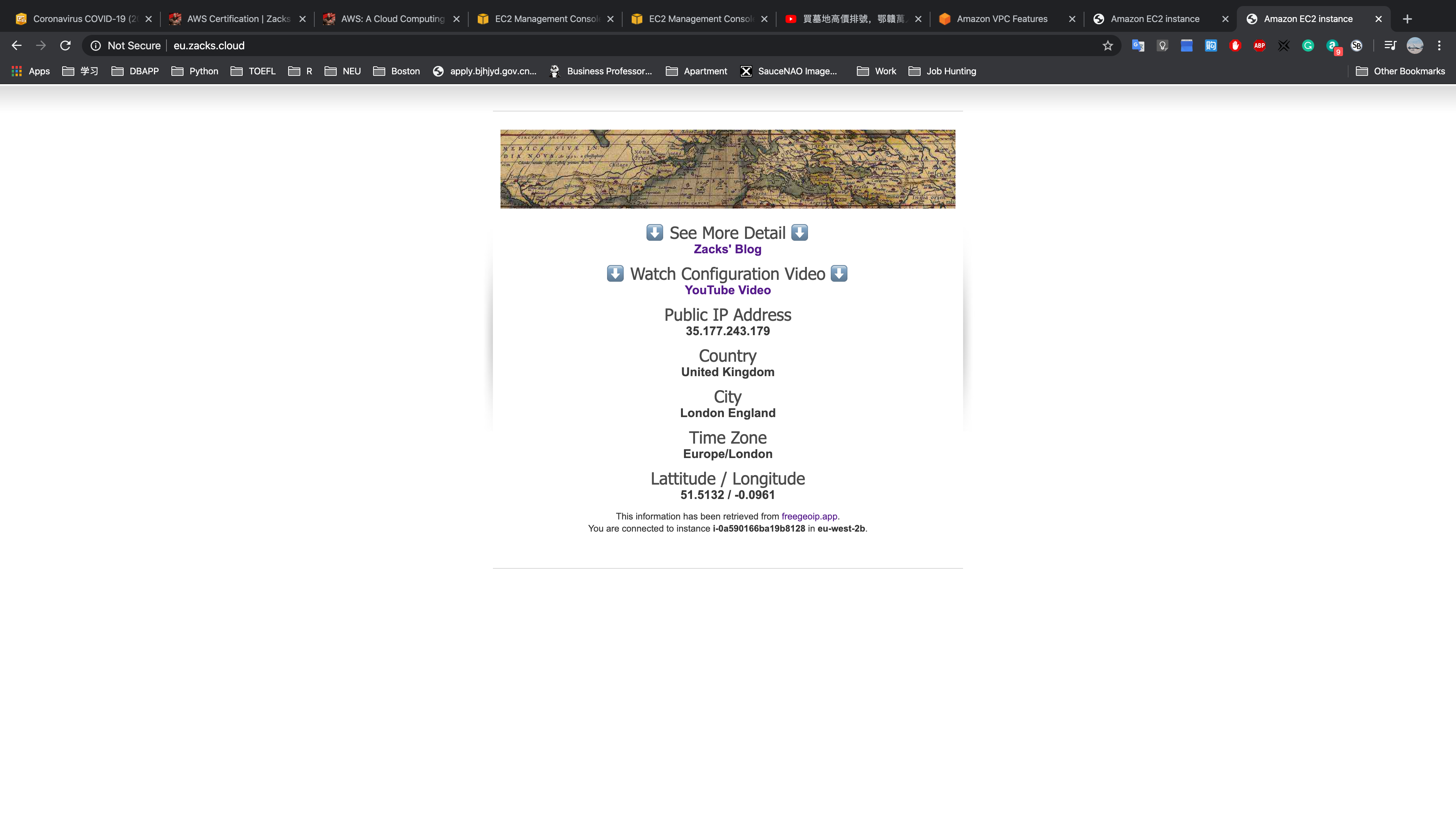
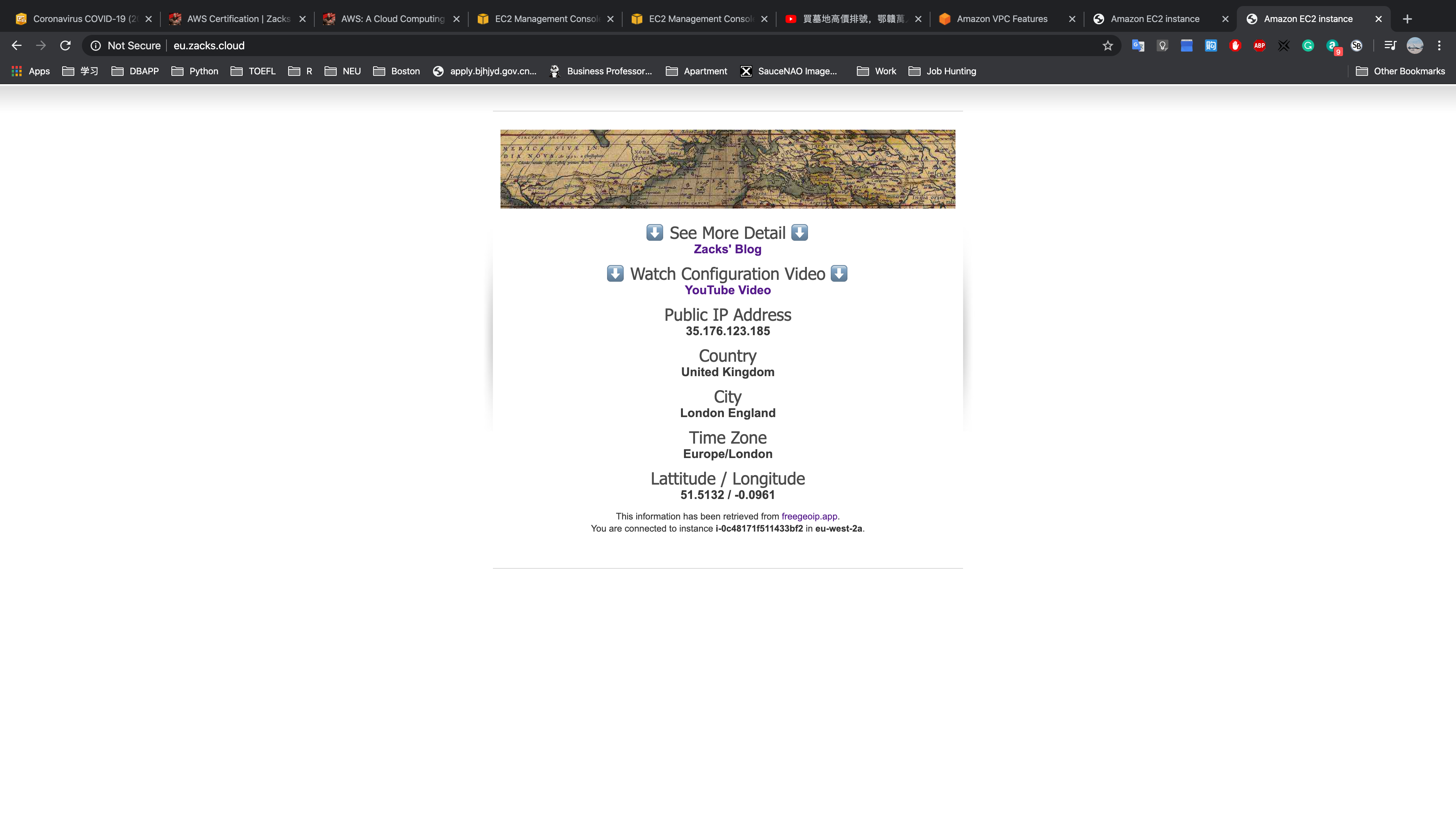
Testing HA
US - EAST - 1 (us.zacks.cloud)
- STOP a instance

- Check Load Balancing
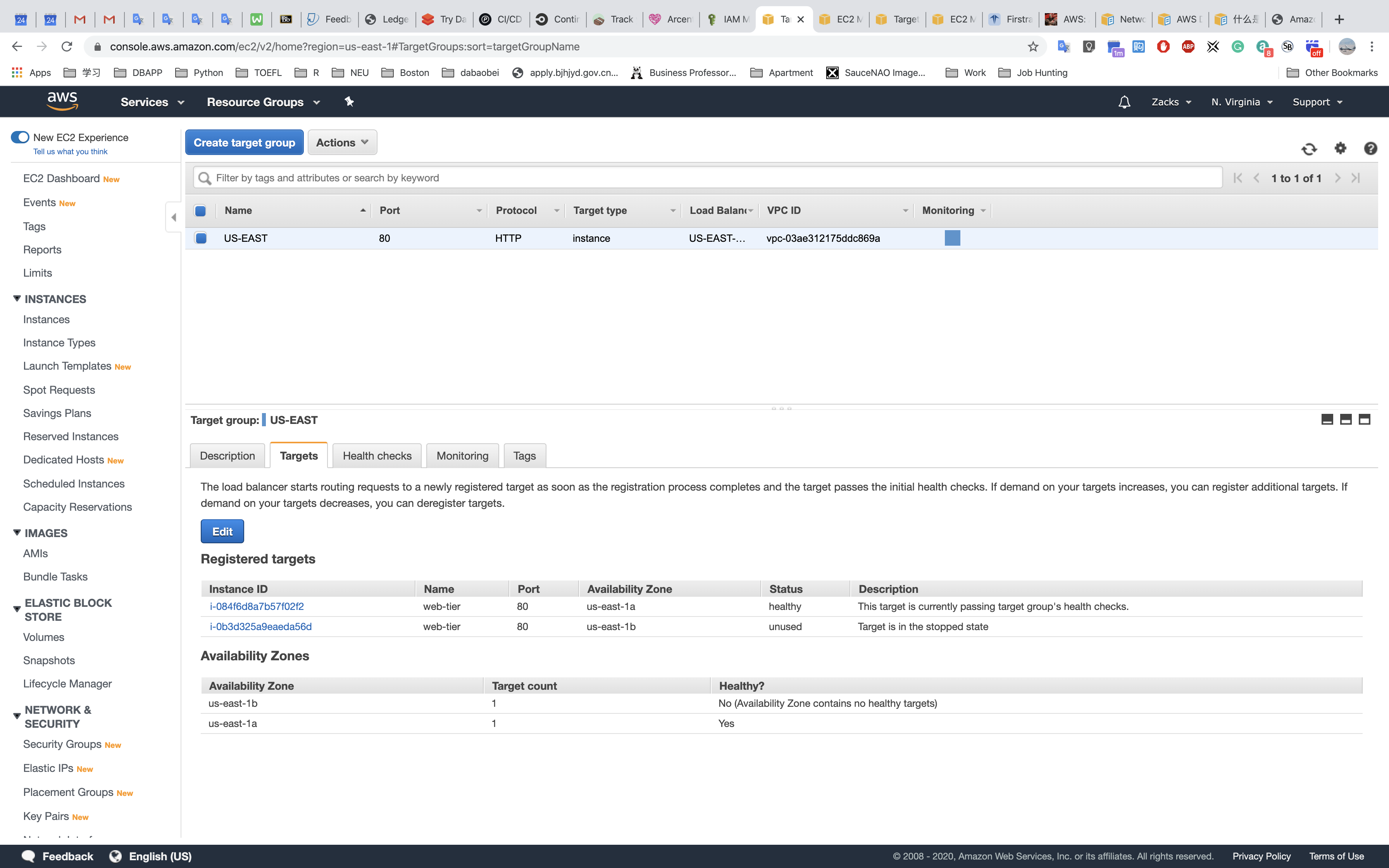
- Check Auto Scaling
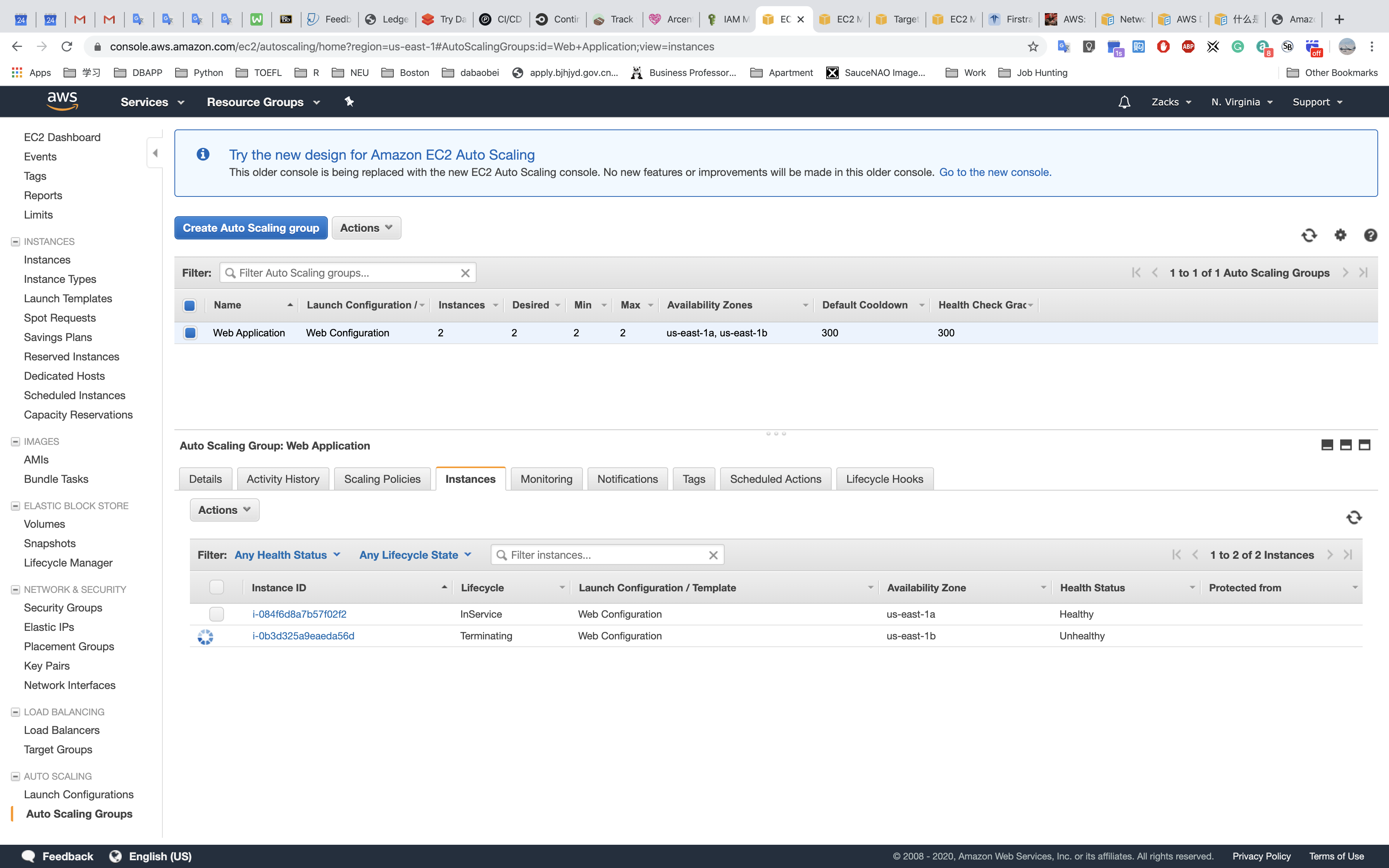
- Check Instances
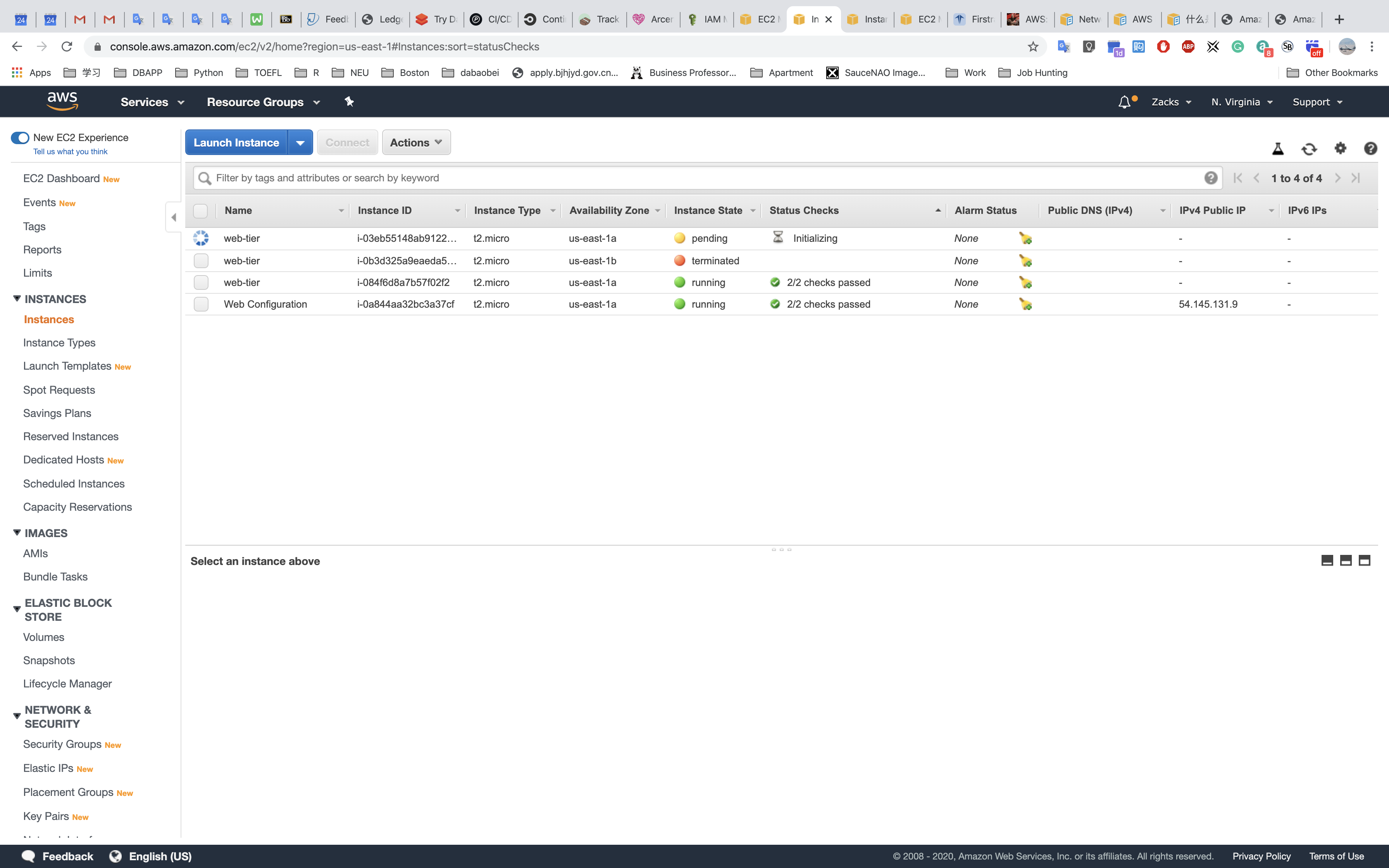
- Test ELB


EU - WEST - 2 (us.zacks.cloud)
- STOP a instance
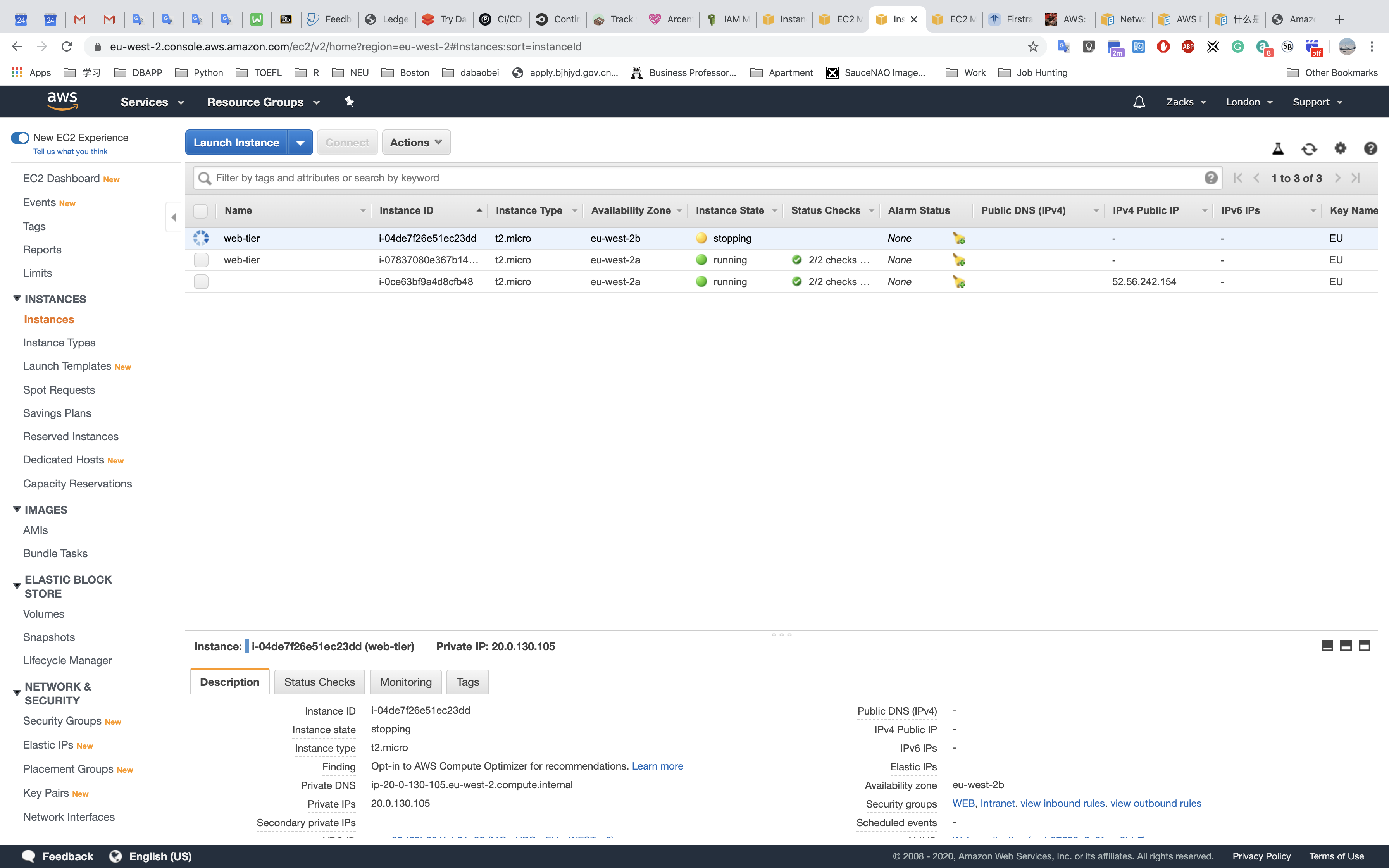
- Check Load Balancing
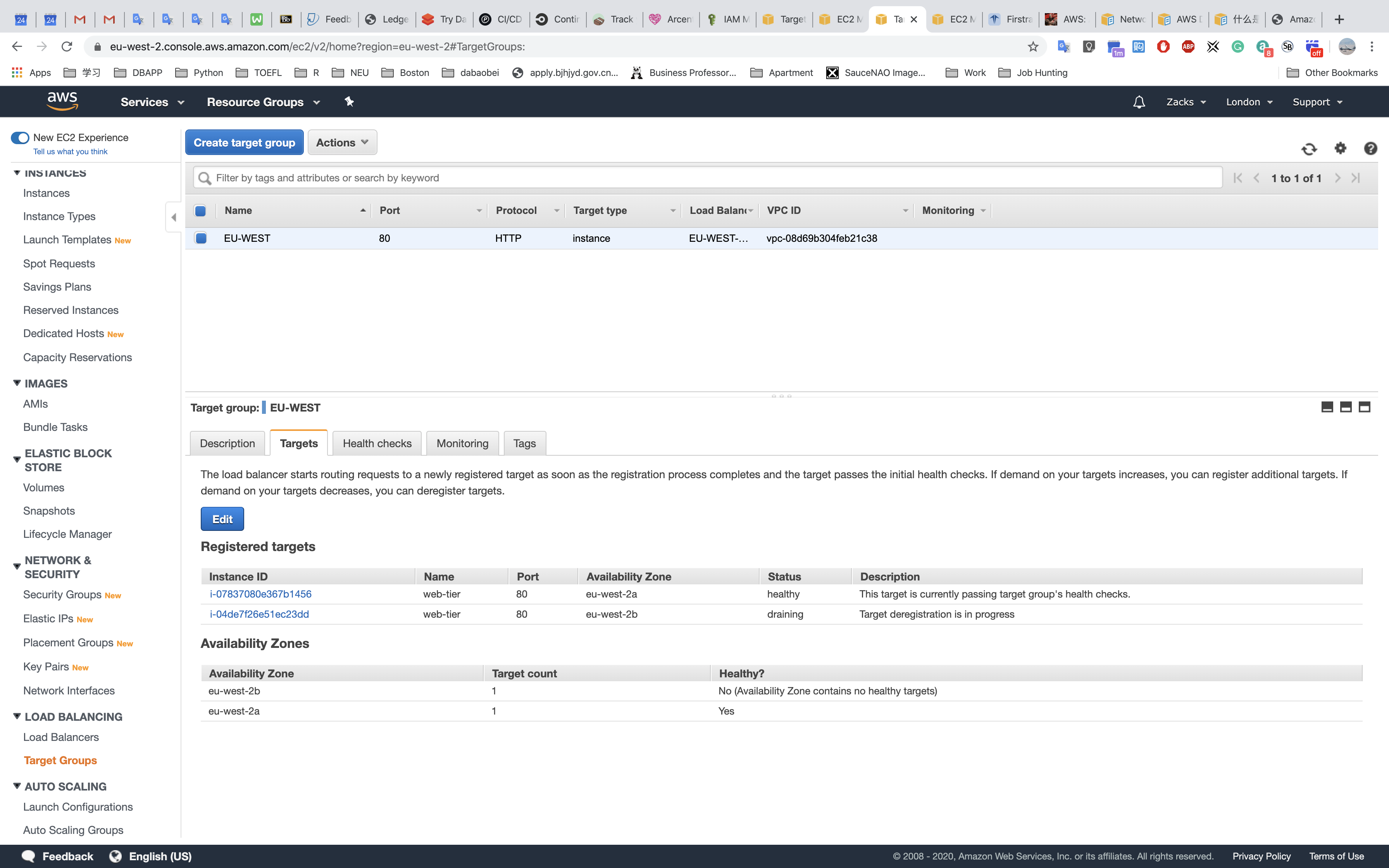
- Check Auto Scaling
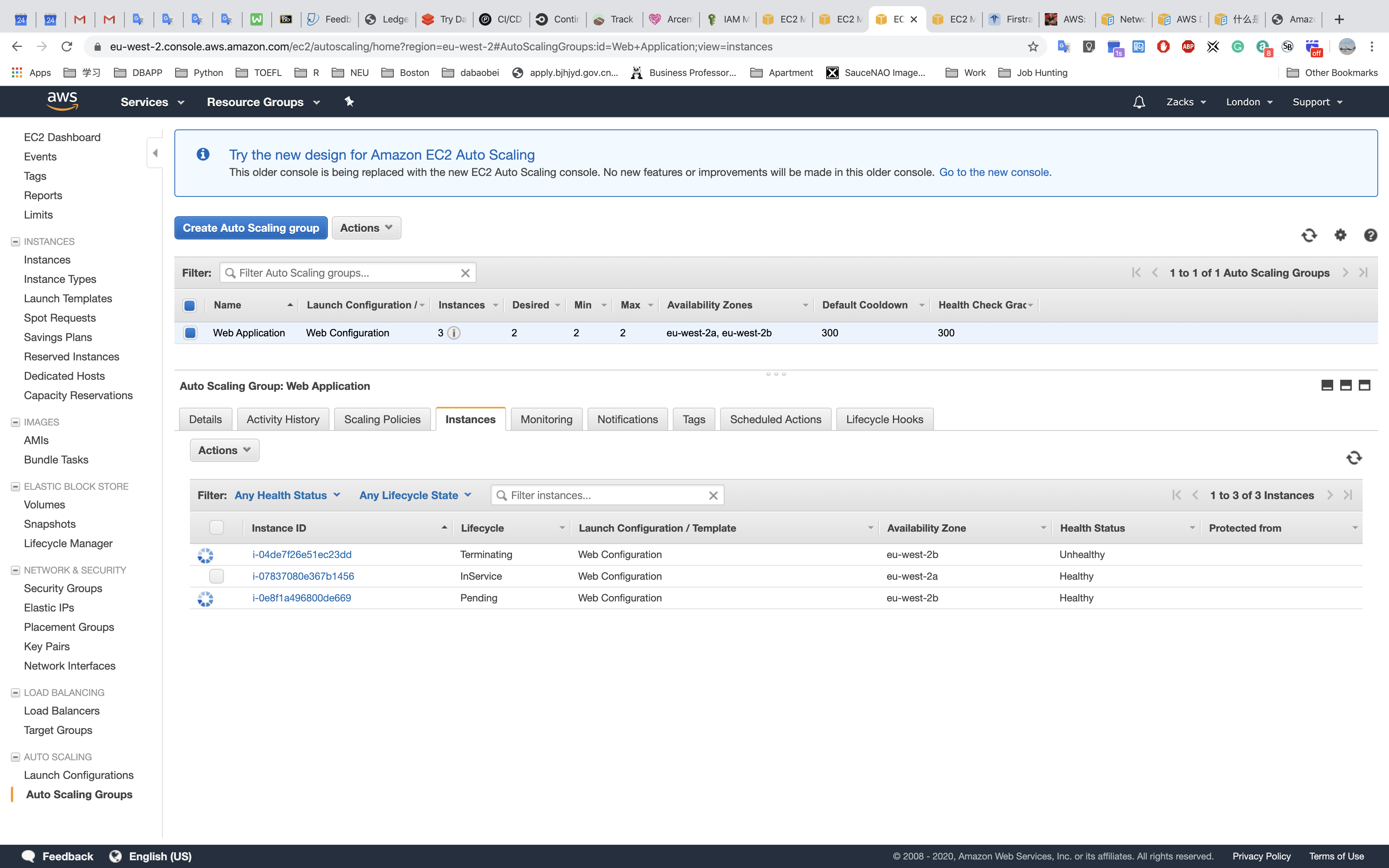
- Check Instances
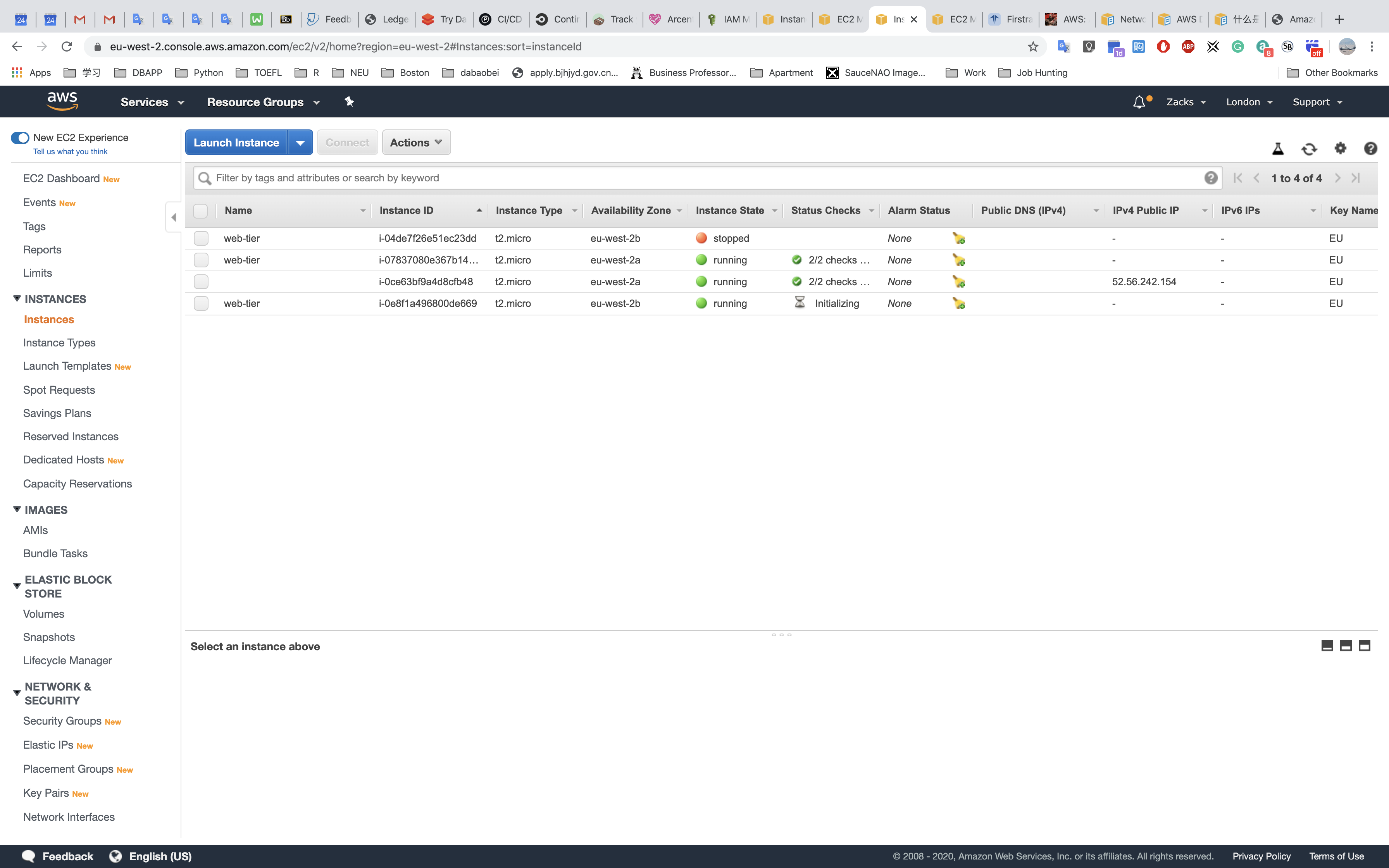
- Test ELB


IAM
System Administrator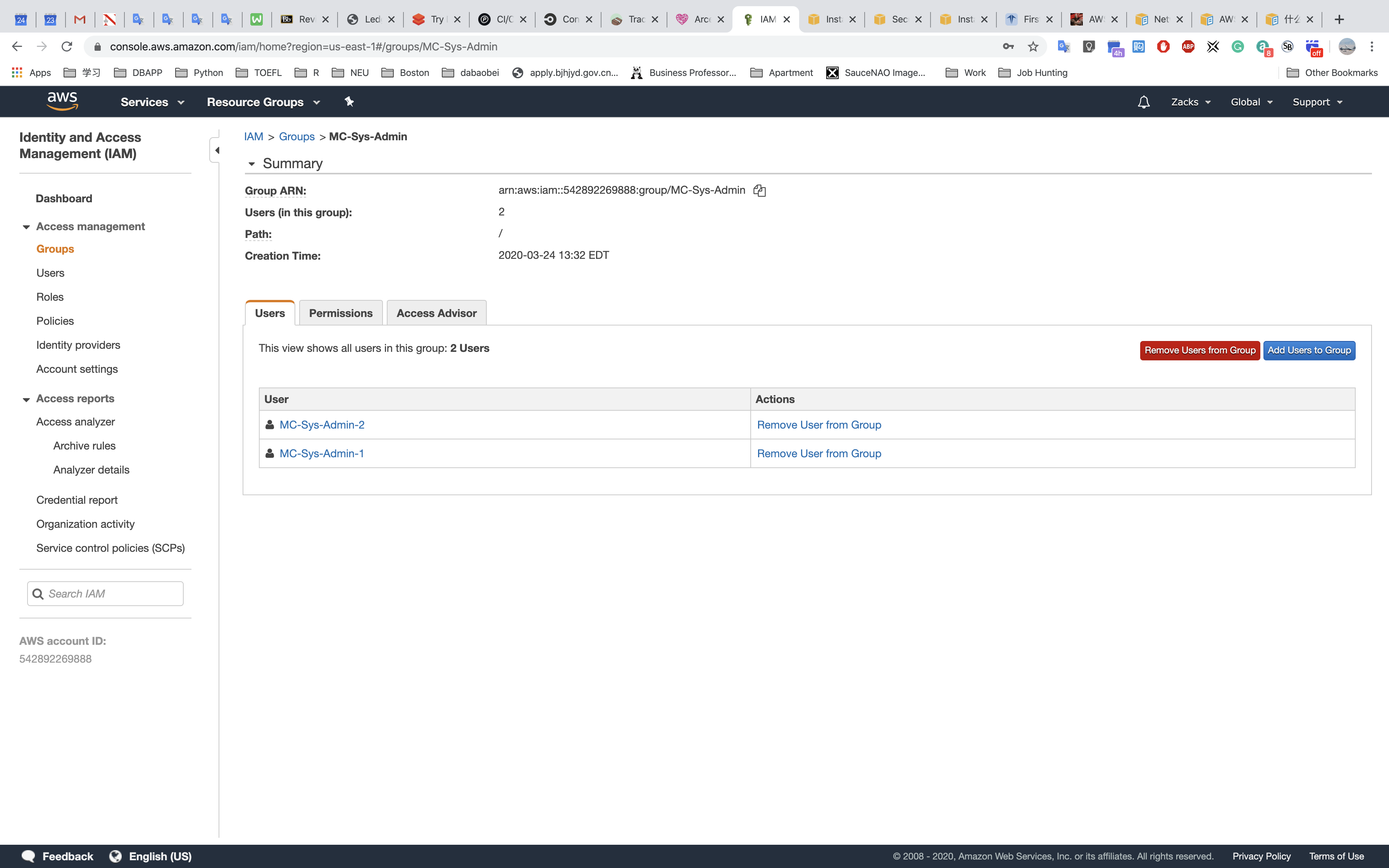
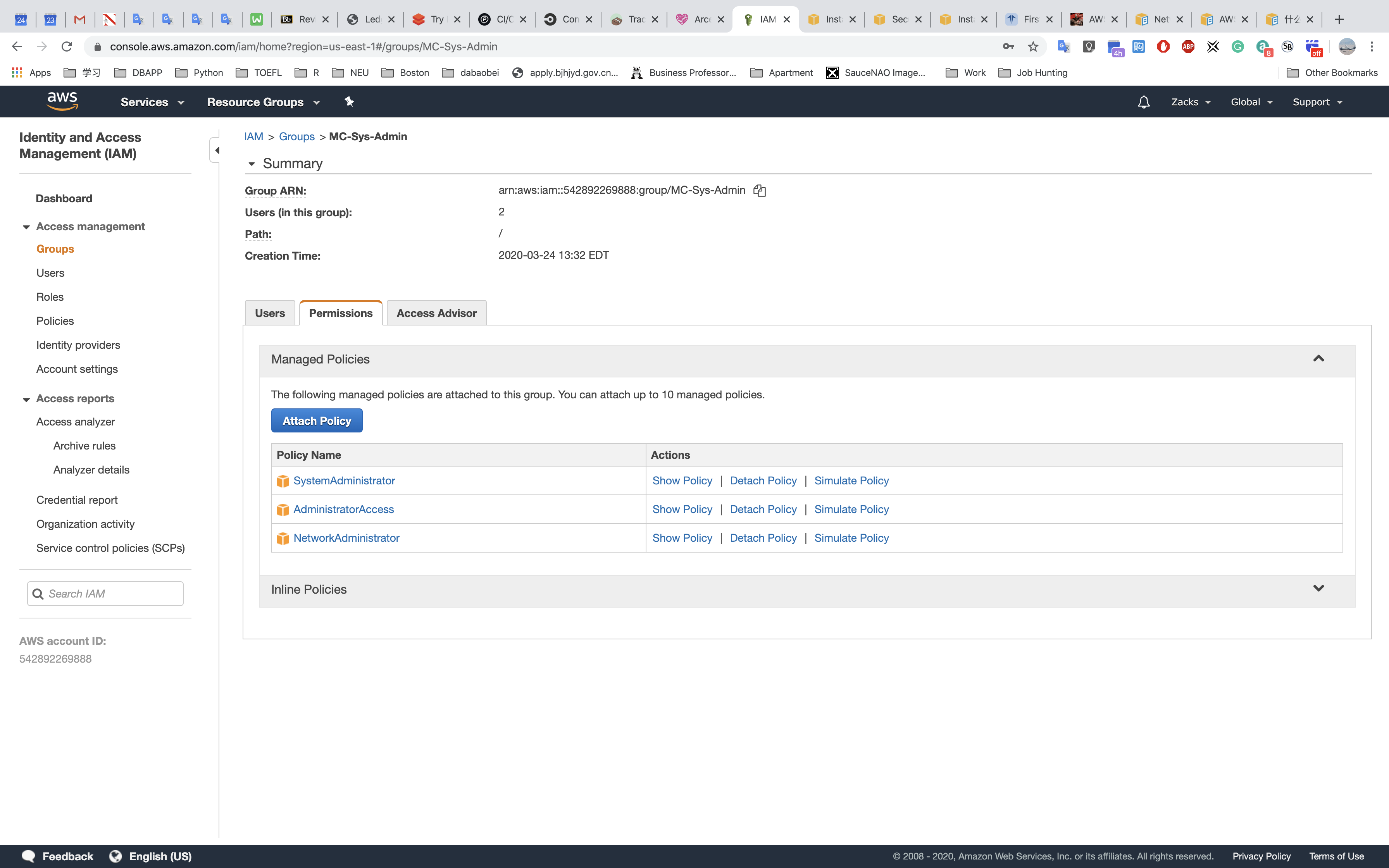
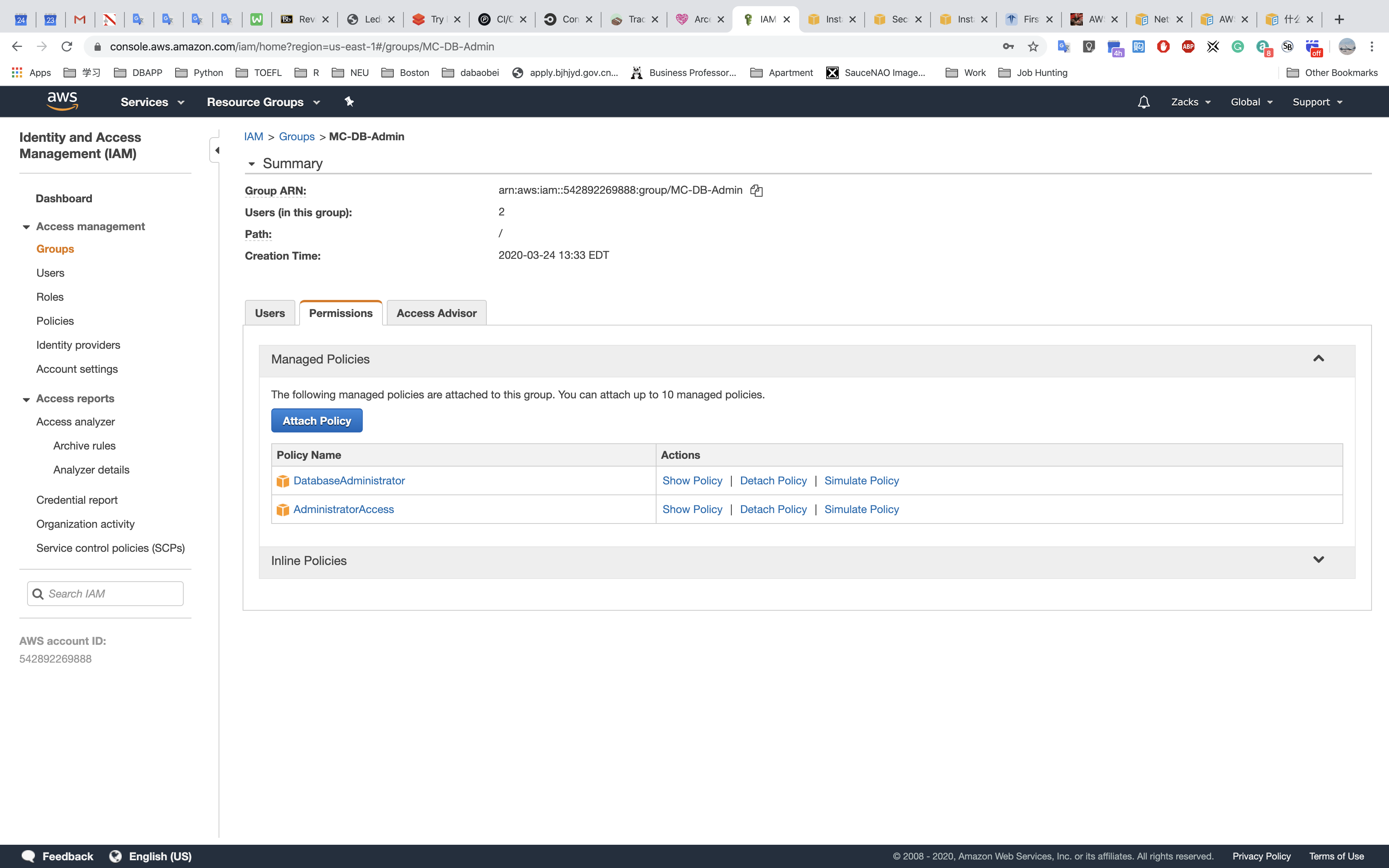
Database Administrator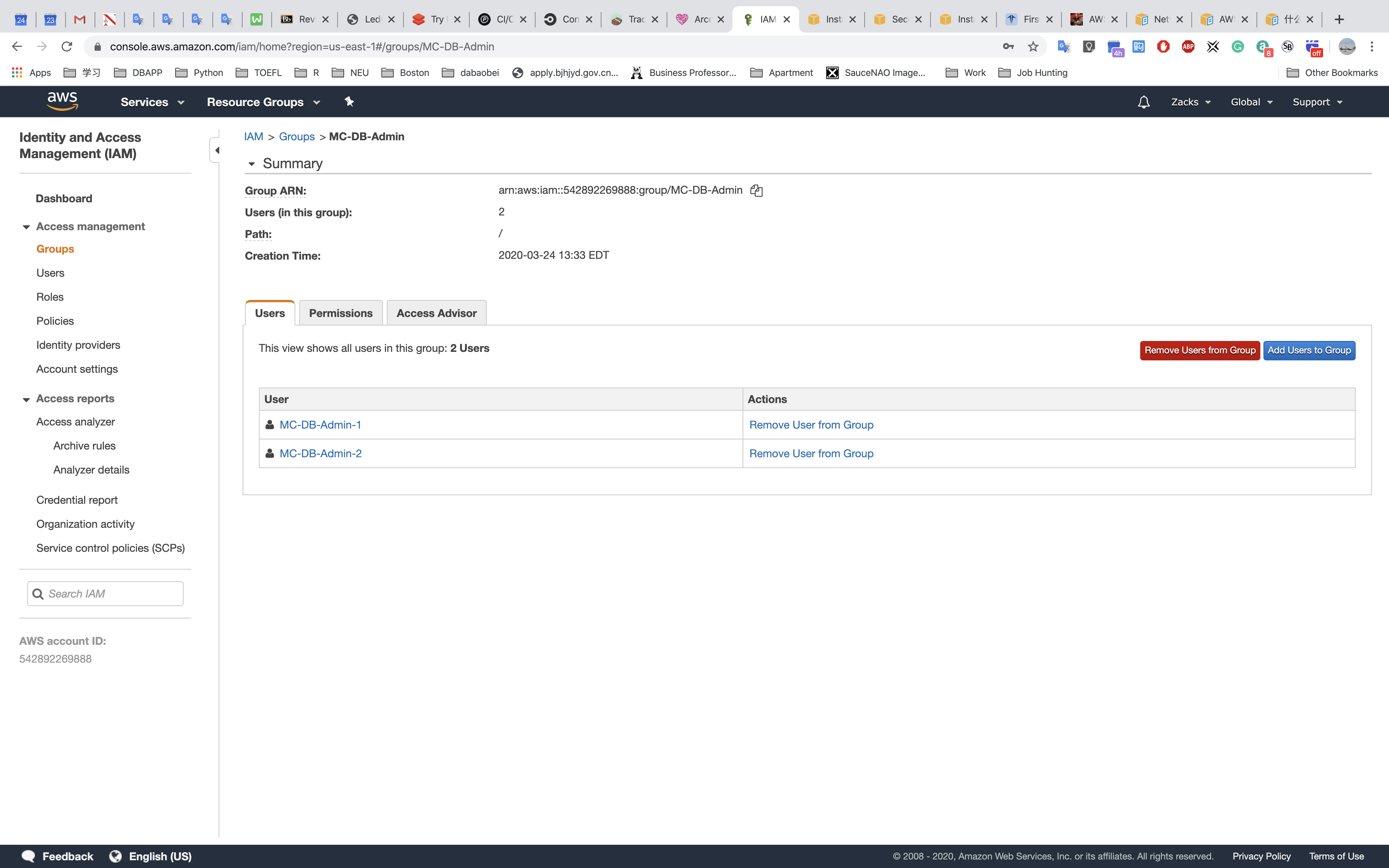
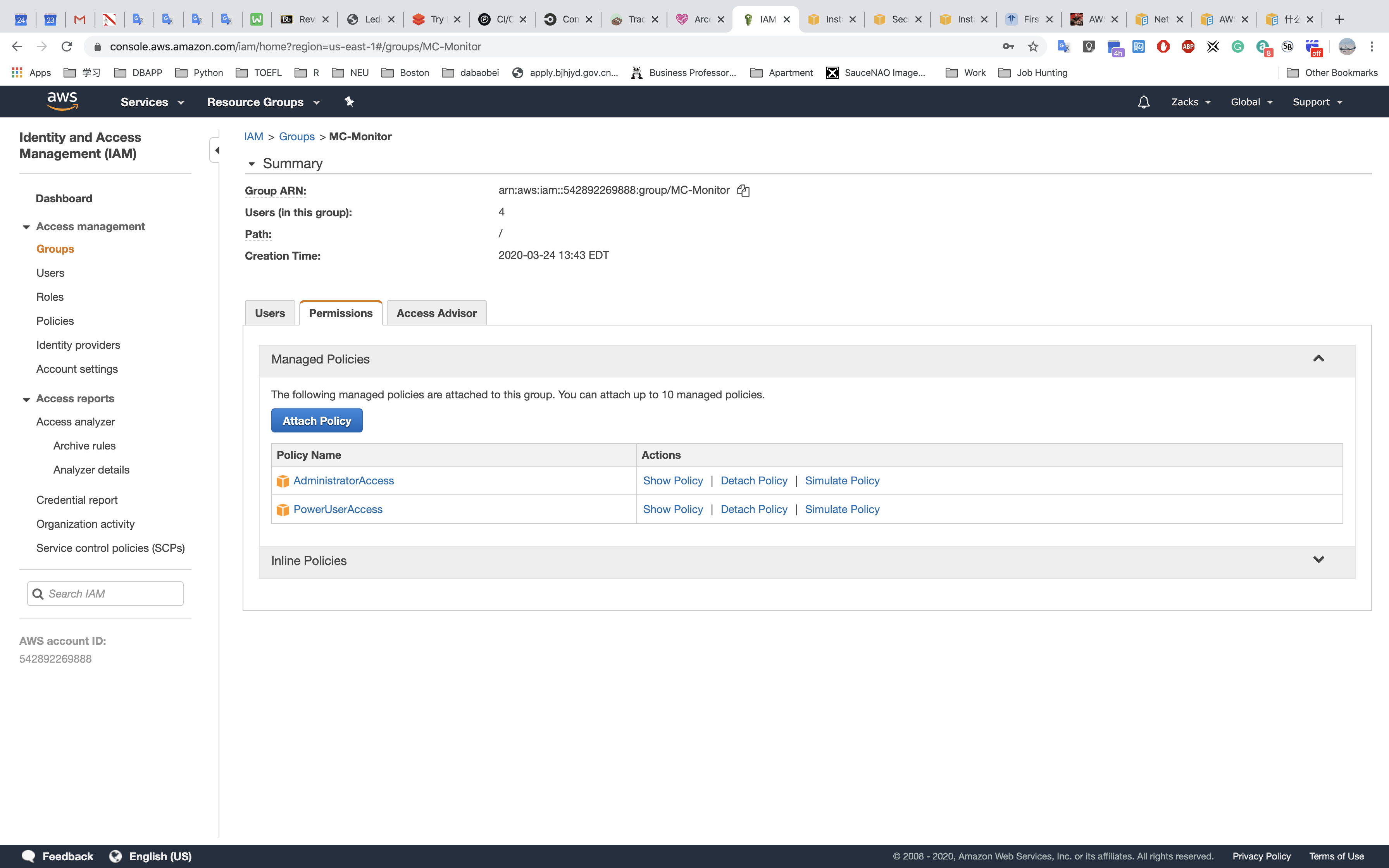
Monitoring Group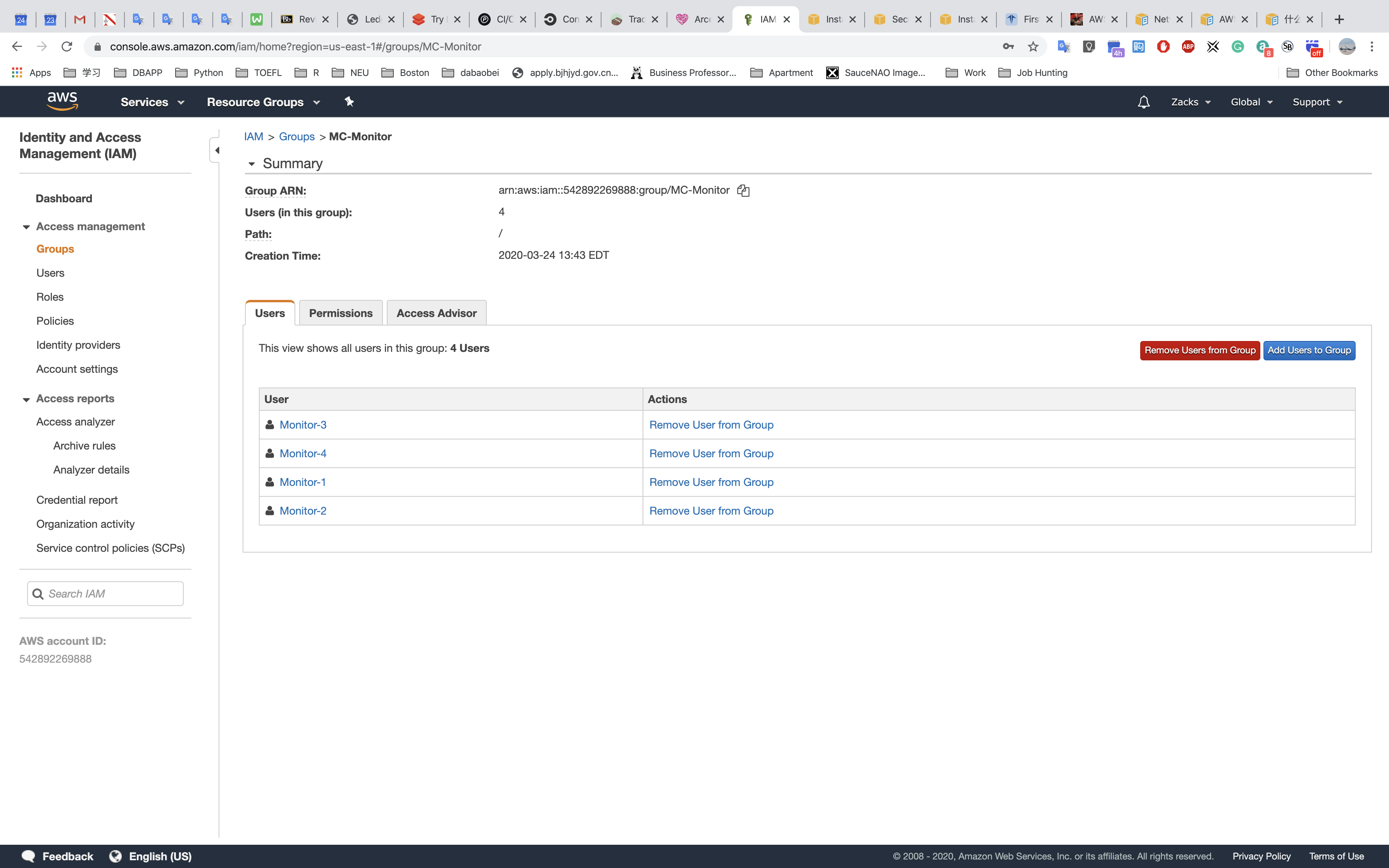
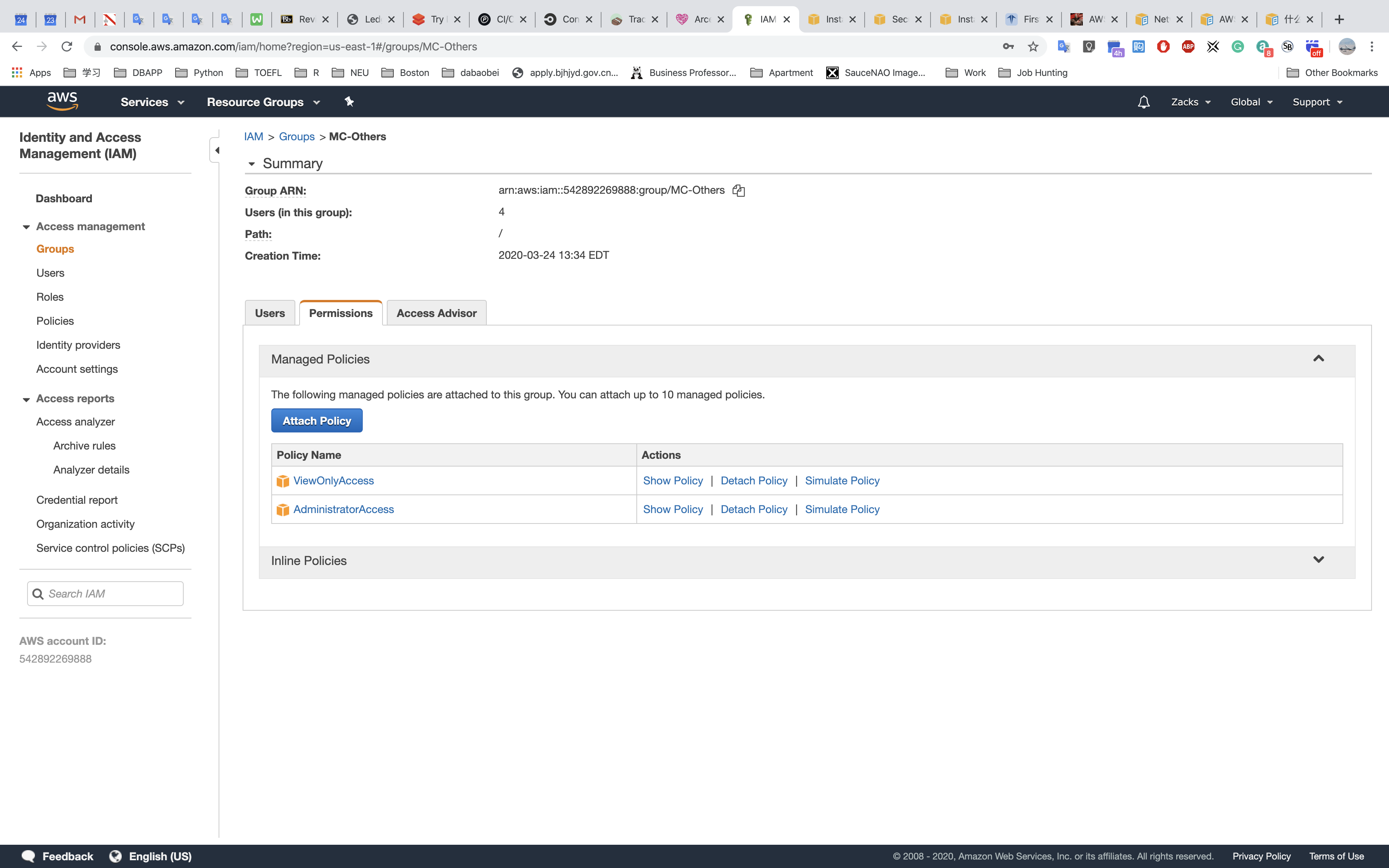
All other users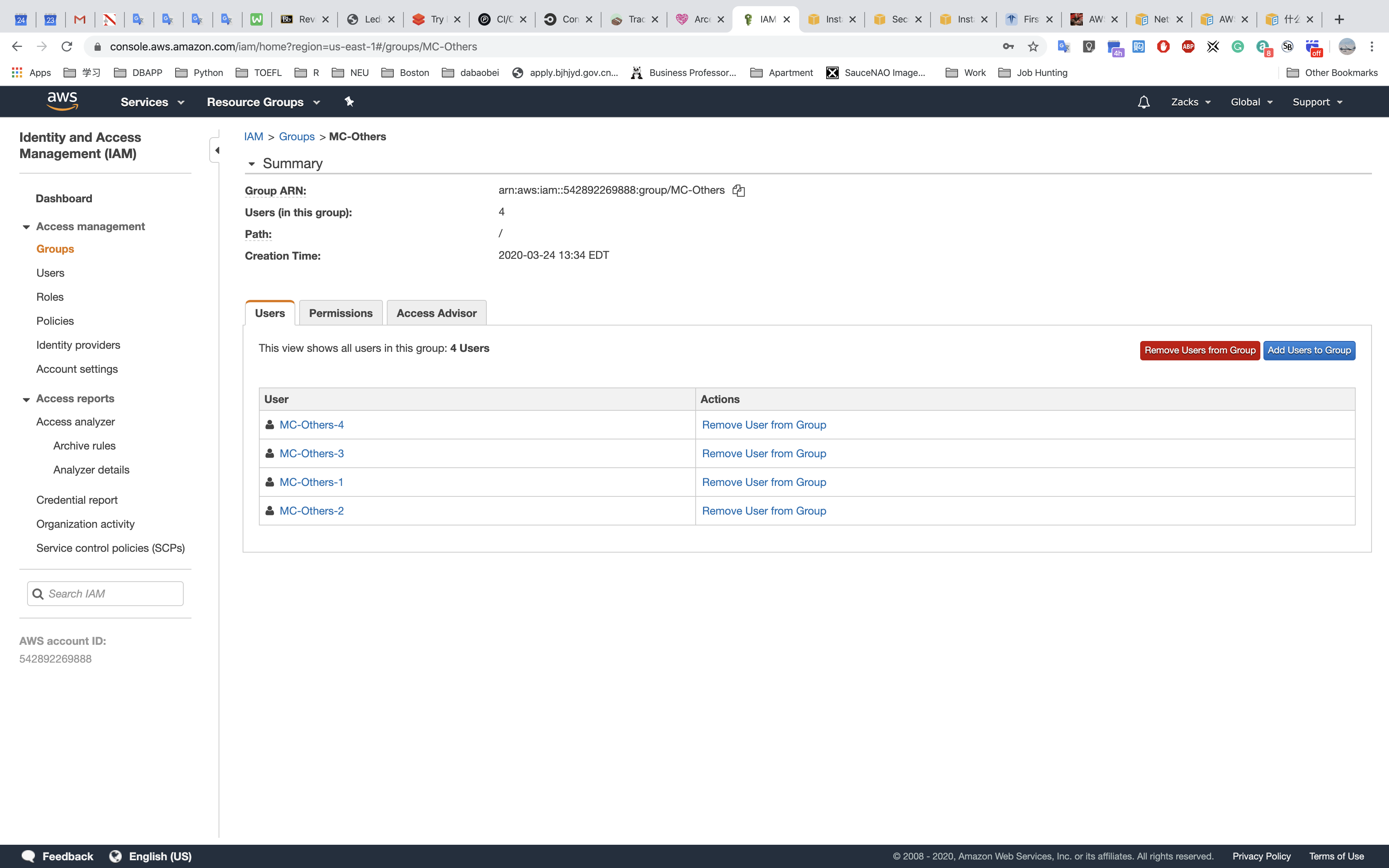
For Virtual MFA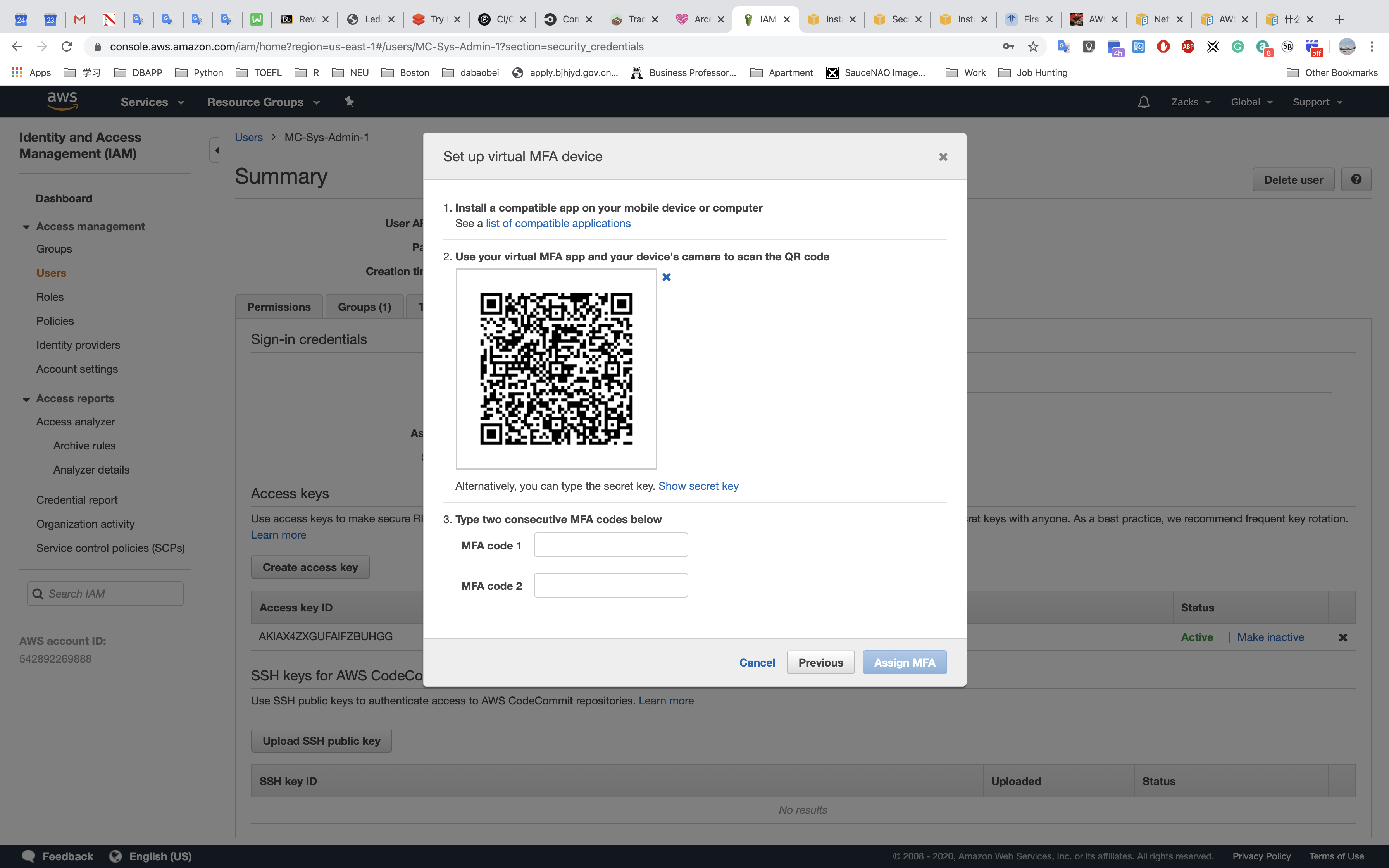
Reference:
Tutorial: Install a LAMP Web Server on Amazon Linux 2
Working with a DB Instance in a VPC
Tutorial: Create an Amazon VPC for Use with a DB Instance
Scenarios for Accessing a DB Instance in a VPC
Using a Load Balancer with an Auto Scaling Group
Attaching a Load Balancer to Your Auto Scaling Group
Getting Started with Amazon Route 53
Routing Traffic to an ELB Load Balancer
Choosing Between Alias and Non-Alias Records
Amazon VPC-to-Amazon VPC Connectivity Options
Updating Your Route Tables for a VPC Peering Connection
Network-to-Amazon VPC Connectivity Options
Contributions
- Danlin Shen
- Setting up the VPC, EC2, RDS MySQL, Route 53, ELB, HA, and IAM
- Writing Papers
- Mingdi Pang
- Setting AWS RDS MS SQL
- Creating Slides.ver2
- Nizamuddin Shaik
- Creating Slides.ver1